We got our first UEFA Women’s Champions League points of the season on the board thanks to goals from Beth Mead and Alessia Russo in Thursday’s 2-0 win away to Benfica.
FIRST HALF
It took until the 19th minute for us to have our first sight…

We got our first UEFA Women’s Champions League points of the season on the board thanks to goals from Beth Mead and Alessia Russo in Thursday’s 2-0 win away to Benfica.
It took until the 19th minute for us to have our first sight…

Everything you need to know for the Lions’ final regular-season match in “The Road Ahead” driven by Audi:
– Pedro Gallese’s next…

The Estée Lauder Companies Inc. (NYSE: EL) will release its fiscal 2026 first quarter results on October 30, 2025.
On that date, at 8:30 a.m. (ET), the Company will provide a live webcast of its conference call and presentation discussing the results, future prospects and recent corporate developments. Stéphane de La Faverie, President and CEO, and Akhil Shrivastava, EVP and CFO, will host the call.
Those wishing to access the webcast can visit http://www.elcompanies.com/investors. The call will be archived on the Company’s website.
The Estée Lauder Companies Inc. is one of the world’s leading manufacturers, marketers and sellers of quality skin care, makeup, fragrance and hair care products, and is a steward of luxury and prestige brands globally. The Company’s products are sold in approximately 150 countries and territories under brand names including: Estée Lauder, Aramis, Clinique, Lab Series, Origins, M·A·C, La Mer, Bobbi Brown Cosmetics, Aveda, Jo Malone London, Bumble and bumble, Darphin Paris, TOM FORD, Smashbox, AERIN Beauty, Le Labo, Editions de Parfums Frédéric Malle, GLAMGLOW, KILIAN
ELC-F
View source version on businesswire.com: https://www.businesswire.com/news/home/20251016457649/en/
Investors: Rainey Mancini
[email protected]
Media: Brendan Riley
[email protected]
Source: The Estée Lauder Companies Inc.

Apple Notes has become one of Apple’s most consistently updated apps, and iOS 26 brought several solid new additions. Here’s everything new for Apple Notes in iOS 26.
Perhaps the biggest…
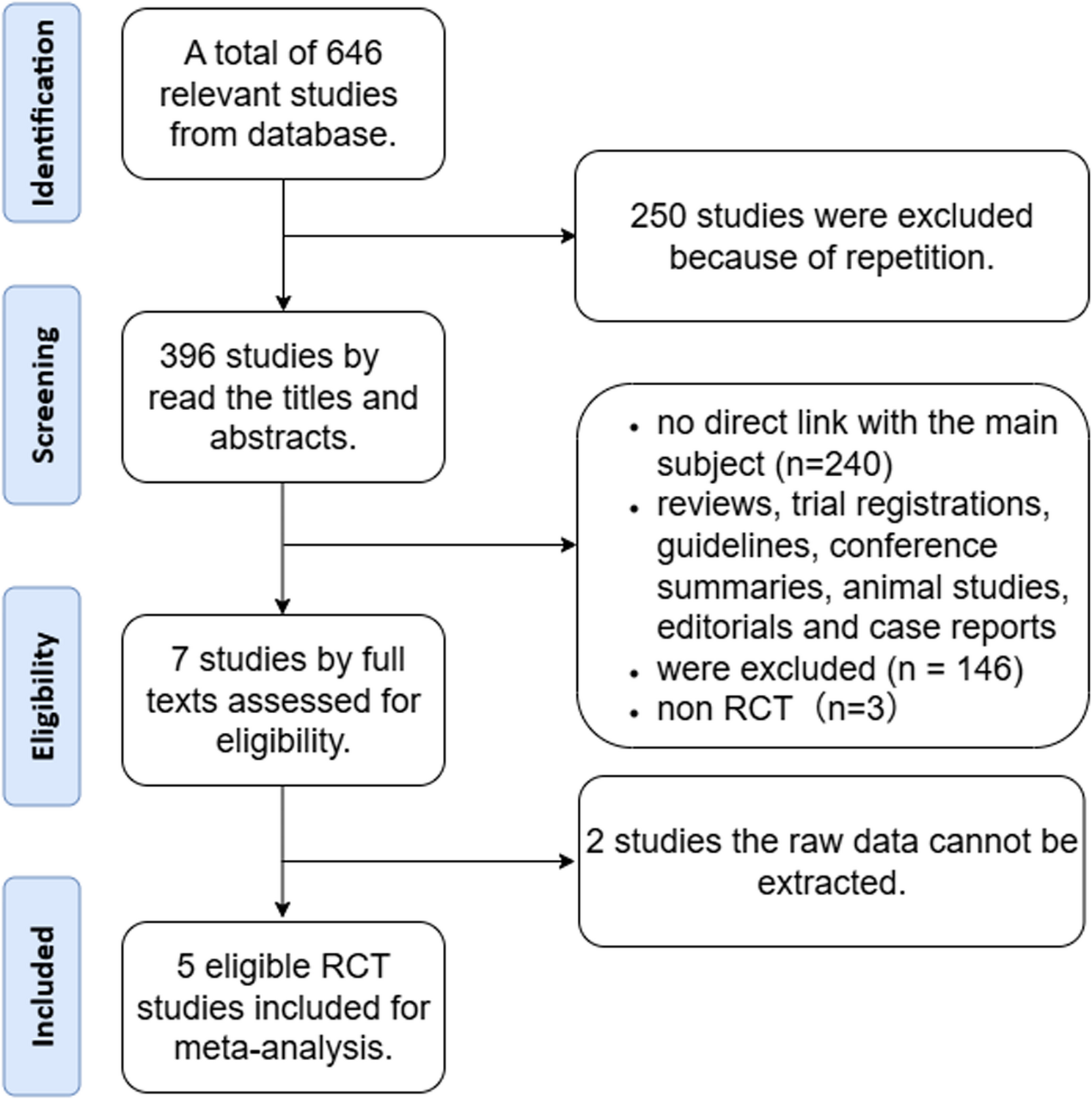
Triki L, Tringali A, Arvanitakis M, Schepis T. Prevention of post-ERCP complications. Best Pract Res Clin Gastroenterol. 2024;69: 101906.
Google Scholar
Akshintala VS, Singh VK. Postendoscopic…
This request seems a bit unusual, so we need to confirm that you’re human. Please press and hold the button until it turns completely green. Thank you for your cooperation!

Lewis Hamilton is hopeful that Ferrari can take a “step forward” by extracting more from their car during the United States Grand Prix weekend, with the seven-time World Champion admitting that the final six races of the campaign could play a…

Thousands of networks—many of them operated by the US government and Fortune 500 companies—face an “imminent threat” of being breached by a nation-state hacking group following the breach of a major maker of software, the federal government warned on Wednesday.
F5, a Seattle-based maker of networking software, disclosed the breach on Wednesday. F5 said a “sophisticated” threat group working for an undisclosed nation-state government had surreptitiously and persistently dwelled in its network over a “long term.” Security researchers who have responded to similar intrusions in the past took the language to mean the hackers were inside the F5 network for years.
During that time, F5 said, the hackers took control of the network segment the company uses to create and distribute updates for BIG IP, a line of server appliances that F5 says is used by 48 of the world’s top 50 corporations. Wednesday’s disclosure went on to say the threat group downloaded proprietary BIG-IP source code information about vulnerabilities that had been privately discovered but not yet patched. The hackers also obtained configuration settings that some customers used inside their networks.
Control of the build system and access to the source code, customer configurations, and documentation of unpatched vulnerabilities has the potential to give the hackers unprecedented knowledge of weaknesses and the ability to exploit them in supply-chain attacks on thousands of networks, many of which are sensitive. The theft of customer configurations and other data further raises the risk that sensitive credentials can be abused, F5 and outside security experts said.
Customers position BIG-IP at the very edge of their networks for use as load balancers and firewalls, and for inspection and encryption of data passing into and out of networks. Given BIG-IP’s network position and its role in managing traffic for web servers, previous compromises have allowed adversaries to expand their access to other parts of an infected network.
F5 said that investigations by two outside intrusion-response firms have yet to find any evidence of supply-chain attacks. The company attached letters from firms IOActive and NCC Group attesting that analyses of source code and build pipeline uncovered no signs that a “threat actor modified or introduced any vulnerabilities into the in-scope items.” The firms also said they didn’t identify any evidence of critical vulnerabilities in the system. Investigators, which also included Mandiant and CrowdStrike, found no evidence that data from its CRM, financial, support case management, or health systems was accessed.
The company released updates for its BIG-IP, F5OS, BIG-IQ, and APM products. CVE designations and other details are here. Two days ago, F5 rotated BIG-IP signing certificates, though there was no immediate confirmation that the move is in response to the breach.

More than 890 cases of dengue reported from Jan 1 to Oct 15, says health minister

Researchers made this discovery while studying a rare…