…


Isack Hadjar admits that the prospect of joining Max Verstappen at Red Bull for the 2026 season “really excites me” as speculation grows about where he will be racing next year.
The Frenchman has impressed in his maiden Formula 1 campaign, which…

Madison Chock and Evan Bates started the 2025-26 figure skating Grand Prix season the same way as they ended the last two two – at the top of the rankings.
Skating to a collection of Lenny Kravitz hits, the USA ice dance couple took the lead…

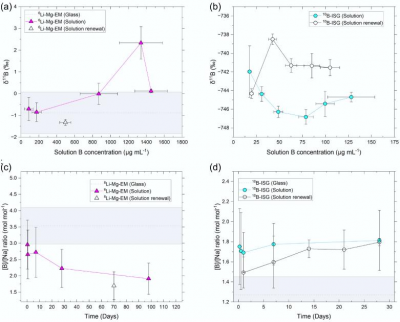
Newswise — By employing boron isotope fingerprinting techniques, the team was able to track the release of boron from two distinct glass compositions, focusing on the role of diffusion through the altered surface…

Colombian racing driver Tatiana Calderon brings a wealth of experience in single-seater racing, including Indycar, Formula 2, GP3, and Super Formula. Currently competing in the 2024 IMSA SportsCar…

WASHINGTON, D.C. (7News) — Researchers at George Washington University are studying artificial intelligence to see if the technology could help people quit smoking.
Smoking is a hard habit to kick. Less than one in 10 adults who smoke…

The final piece of China’s cross-border data transfer framework has now been released with the issuance of the Certification Measures. Effective January 1, 2026, businesses must closely monitor certification institutions, standards, and application procedures. Early preparation and strategic planning will be essential for long-term compliance and risk management.
On October 14, 2025, the Cyberspace Administration of China (CAC) and the State Administration for Market Regulation (SAMR) jointly issued the long-awaited Measures for Certification of Cross-Border Personal Information Transfer (hereinafter referred to as the “Measures”), which will officially take effect on January 1, 2026.
The release of the Measures marks a pivotal moment in China’s data governance landscape. It completes the three-pathway framework for cross-border personal information transfers established under the Personal Information Protection Law (PIPL).
Find Business Support
With the certification method now fully defined, China’s regulatory architecture for cross-border data transfer (CBDT) is considered comprehensive and operational.
The Measures clarify key aspects of the certification process, including scope and applicability, application procedures, certification body obligations, as well as supervision and enforcement.
This final regulatory piece enhances legal certainty for businesses. It offers enterprises another structured compliance pathway and may prove especially beneficial for multinational corporations engaged in frequent or large-scale data transfers.
Under Article 38 of PIPL, personal information processors in China who need to transfer personal data overseas for business or operational purposes must choose one of three legally prescribed pathways:
Since 2022, China has gradually built out this framework through a series of regulatory instruments. The Security Assessment Measures, released in July 2022, laid out detailed procedures for high-risk data transfers. In February 2023, the Standard Contract Measures were issued and came into effect in June, providing a more accessible compliance route for many businesses.
Find Business Support

However, the certification pathway remained incomplete for some time. While several technical standards and guidelines were released – such as the Security Certification Specifications for Cross-Border Processing of Personal Information V2.0 (December 2022) and the Information Security Technology – Certification Requirements for Cross-Border Transmission of Personal Information (March 2023) – a formal regulatory document was still missing.
Now with the release of the Measures, this long-awaited document provides the legal and procedural foundation for certification, aligning with earlier standards and the CAC’s January 2025 draft for public consultation.
Moreover, China’s State Administration for Market Regulation (SAMR) and Standardization Administration of China (SAC) jointly released the Data security technology—Security certification requirements for cross-border processing activity of personal information (GB/T 46068-2025), which will take effect on March 1, 2026.
All these developments signal that the three pathways for CBDT under the PIPL are now fully operational, marking a significant milestone in China’s data governance regime.
The newly released Measures for Certification of Cross-Border Personal Information Transfer outline the specific conditions under which personal information processors may opt for the certification pathway to legally transfer personal data overseas.
To be eligible for certification, a personal information processor must meet all of the following criteria:
Importantly, the Measures prohibit data volume splitting or other circumvention tactics to avoid the security assessment requirement. If the data transfer volume exceeds the thresholds for certification, the processor must undergo a security assessment instead.
Before applying for certification, personal information processors must fulfill several legal obligations, including:
The PIPIA must evaluate:
The PIPIA report should be retained for at least three years.
Also read: How to Conduct a Personal Information Protection Impact Assessment in China
Processors must apply for certification through a professional certification institution authorized to conduct personal information protection audits. For overseas processors, the application must be submitted via a designated domestic representative or entity.
Once the application is approved, the institution will issue a certificate, valid for three years. To maintain continuity, processors must reapply six months before the certificate expires.


The Measures establish a multi-layered oversight mechanism:
Under China’s CBDT mechanisms, both the standard contract and certification pathways provide legal mechanisms for cross-border transfers of personal information. While they share many similarities, such as overlapping applicability and similar pre-transfer obligations, their structural differences make them suitable for distinct business scenarios.
The standard contract is a self-managed process in which enterprises sign a fixed-format agreement with the overseas recipient, strictly following the CAC’s template. After conducting a self-assessment, the enterprise submits the contract and related materials for filing with the provincial CAC, which may conduct formal or substantive reviews. As a commercial agreement, the standard contract is not publicly disclosed, and its contents are not subject to public scrutiny or external evaluation.
In contrast, certification is conducted by third-party professional institutions based on CAC-issued rules. It involves a comprehensive review of the enterprise’s technical, organizational, and governance measures. Unlike the standard contract, certification carries a degree of public authority – it reflects, to some extent, administrative recognition of the enterprise’s data protection capabilities. For companies with high reputational stakes in personal information protection, certification offers a credible external endorsement of their compliance posture.
Find Business Support

The compliance focus also differs. The standard contract emphasizes the legal obligations of a specific data transfer, ensuring the overseas recipient agrees to uphold data subject rights and assumes clear data protection responsibilities. Certification, on the other hand, assesses the enterprise’s overall compliance framework, including internal governance, data protection systems, and technical safeguards. It promotes ongoing compliance and dynamic supervision. In practice, the standard contract is more suited to “one-off” or occasional transfers, while certification is better aligned with enterprises engaged in frequent or long-term cross-border data activities.
Post-transfer supervision further distinguishes the two. With the standard contract, enterprises are responsible for monitoring the overseas recipient’s compliance, and CAC oversight is primarily conducted through the filing system. Certification bodies, however, implement continuous monitoring mechanisms. Certificates may be suspended or revoked, and violations are publicly disclosed, creating external compliance pressure.
Given these differences, the standard contract is generally more appropriate for low-volume, low-risk transfers. It is relatively easy to implement but offers limited flexibility due to its fixed format. Certification, by contrast, is better suited for enterprises with frequent, high-risk, or high-profile data transfers, or those seeking to demonstrate a high level of data protection. The certification is valid for three years, helping reduce repetitive compliance efforts.
Enterprises should assess their business scale, data export scenarios, and compliance capacity to select the most appropriate pathway for CBDT.
| Aspect | Standard Contract | Certification |
| Legal nature and review mechanism | Enterprises sign a fixed-format agreement with the overseas recipient, following CAC’s template.
Self-assessment and filing with provincial CAC; subject to formal or substantive review. |
Conducted by third-party institutions under CAC rules. Reviews technical, organizational, and governance measures. Carries independent credibility. |
| Compliance focus and depth | Focuses on contractual obligations. Ensures overseas recipient upholds data subject rights and assumes data protection responsibilities. | Evaluates full compliance framework, including governance, systems, and safeguards.
Emphasizes ongoing and dynamic compliance. |
| Post-transfer supervision and accountability | Enterprises monitor recipients’ compliance. CAC oversight via the filing system. | Certification bodies provide continuous monitoring (e.g., annual inspection). Certificates may be suspended or revoked; violations are publicly disclosed. |
| Applicability and flexibility | Best for low-volume, low-risk transfers. Easy to implement, but limited flexibility due to fixed format. | Suited for frequent or high-risk transfers. Valid for three years, reducing repetitive compliance. |
| Cost | Self-declaration will not incur any cost
|
The certification body will charge relevant fees.
|
As the Measures prepare to take effect on January 1, 2026, enterprises should go beyond understanding the basic provisions and actively monitor several key developments to ensure compliant and efficient implementation.
Key areas to monitor include:
Companies are suggested to consult the official websites of the CAC, SAMR, and the Certification and Accreditation Administration of China (CNCA) for timely updates and implementation guidance.
Personal information protection certification is a critical mechanism for enabling compliant, trustworthy, and internationally aligned data flows. As the Measures enter into force in 2026, enterprises must pay close attention to the qualifications of certification institutions, evolving standards and procedures, and long-term compliance obligations. For legal, compliance, and information security professionals, now is the time to study regulatory trends, plan ahead, and strengthen internal capabilities to ensure a smooth transition into the new regime.
If you need further interpretation or practical support, our team at Dezan Shira & Associates is here to assist you with tailored guidance and hands-on expertise. For more information, please get in touch with China@dezshira.com.

Disgraced Lostprophets singer Ian Watkins died after being stabbed in the neck in a alleged prison attack, an inquest has heard.
Watkins, 48, died on 11 October after being assaulted at HMP Wakefield, where he had been serving a 29-year sentence…