Triki L, Tringali A, Arvanitakis M, Schepis T. Prevention of post-ERCP complications. Best Pract Res Clin Gastroenterol. 2024;69: 101906.
Google Scholar
Akshintala VS, Singh VK. Postendoscopic…
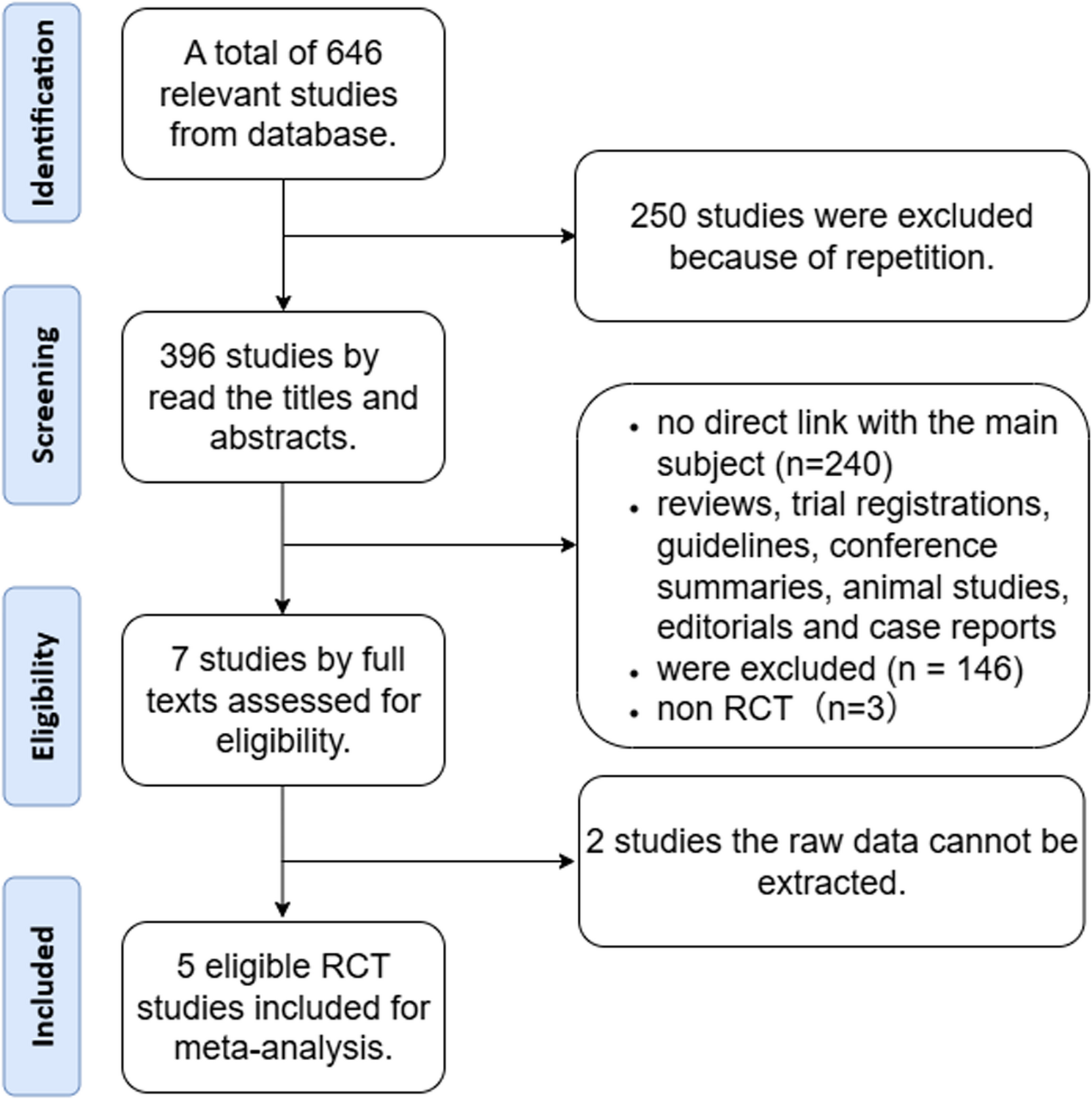
Triki L, Tringali A, Arvanitakis M, Schepis T. Prevention of post-ERCP complications. Best Pract Res Clin Gastroenterol. 2024;69: 101906.
Google Scholar
Akshintala VS, Singh VK. Postendoscopic…
This request seems a bit unusual, so we need to confirm that you’re human. Please press and hold the button until it turns completely green. Thank you for your cooperation!

Lewis Hamilton is hopeful that Ferrari can take a “step forward” by extracting more from their car during the United States Grand Prix weekend, with the seven-time World Champion admitting that the final six races of the campaign could play a…

Thousands of networks—many of them operated by the US government and Fortune 500 companies—face an “imminent threat” of being breached by a nation-state hacking group following the breach of a major maker of software, the federal government warned on Wednesday.
F5, a Seattle-based maker of networking software, disclosed the breach on Wednesday. F5 said a “sophisticated” threat group working for an undisclosed nation-state government had surreptitiously and persistently dwelled in its network over a “long term.” Security researchers who have responded to similar intrusions in the past took the language to mean the hackers were inside the F5 network for years.
During that time, F5 said, the hackers took control of the network segment the company uses to create and distribute updates for BIG IP, a line of server appliances that F5 says is used by 48 of the world’s top 50 corporations. Wednesday’s disclosure went on to say the threat group downloaded proprietary BIG-IP source code information about vulnerabilities that had been privately discovered but not yet patched. The hackers also obtained configuration settings that some customers used inside their networks.
Control of the build system and access to the source code, customer configurations, and documentation of unpatched vulnerabilities has the potential to give the hackers unprecedented knowledge of weaknesses and the ability to exploit them in supply-chain attacks on thousands of networks, many of which are sensitive. The theft of customer configurations and other data further raises the risk that sensitive credentials can be abused, F5 and outside security experts said.
Customers position BIG-IP at the very edge of their networks for use as load balancers and firewalls, and for inspection and encryption of data passing into and out of networks. Given BIG-IP’s network position and its role in managing traffic for web servers, previous compromises have allowed adversaries to expand their access to other parts of an infected network.
F5 said that investigations by two outside intrusion-response firms have yet to find any evidence of supply-chain attacks. The company attached letters from firms IOActive and NCC Group attesting that analyses of source code and build pipeline uncovered no signs that a “threat actor modified or introduced any vulnerabilities into the in-scope items.” The firms also said they didn’t identify any evidence of critical vulnerabilities in the system. Investigators, which also included Mandiant and CrowdStrike, found no evidence that data from its CRM, financial, support case management, or health systems was accessed.
The company released updates for its BIG-IP, F5OS, BIG-IQ, and APM products. CVE designations and other details are here. Two days ago, F5 rotated BIG-IP signing certificates, though there was no immediate confirmation that the move is in response to the breach.

Warner Bros Discovery has rebuked a pledge signed by more than 4,000 film industry figures to not work with Israeli film institutions “implicated in the genocide and apartheid against the Palestinian people”, saying that such a pledge would…
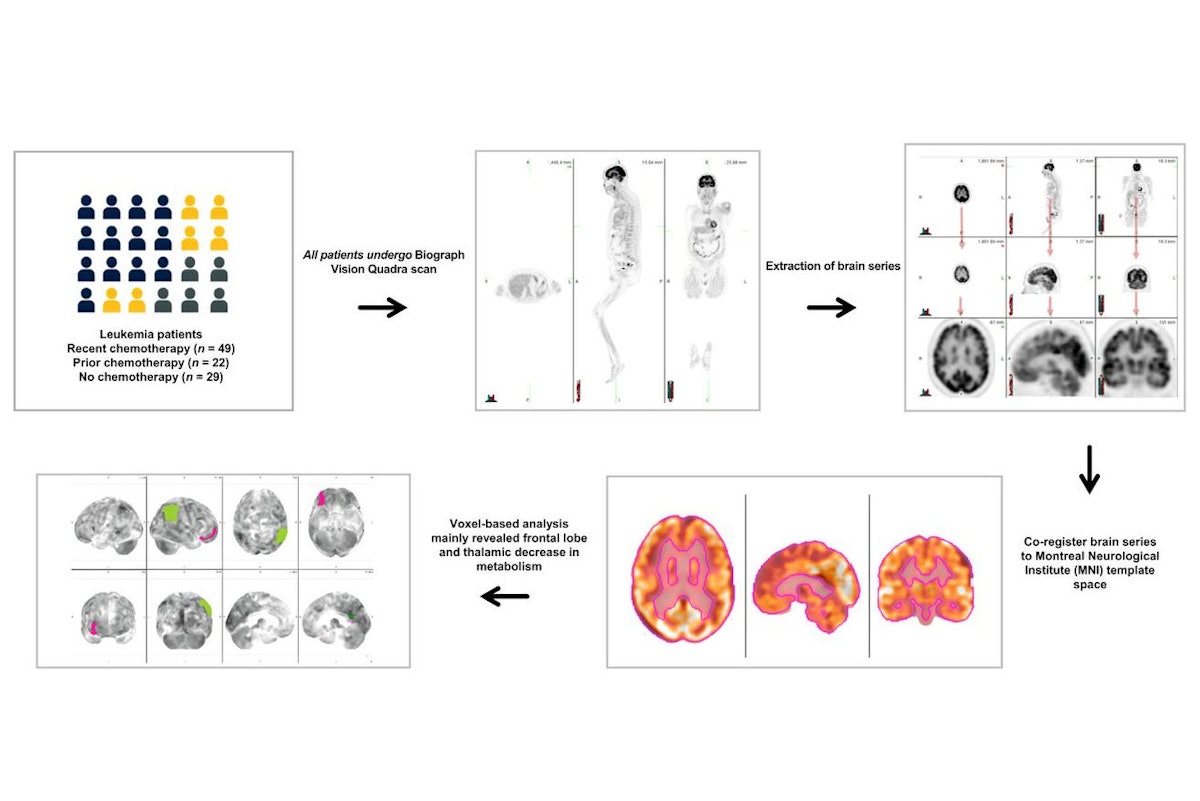
PET/CT imaging has revealed brain regions in leukemia patients with lower glucose metabolism after chemotherapy, according to a study published October 16 in the Journal of Nuclear Medicine.
The findings support research into metabolic imaging…


It took nearly 20 minutes and more than 20 bids between several specialists on the phone and a bidder in the room, but Sotheby’s came away with at least one major win at Thursday’s contemporary art evening sale. That victory lot was Francis…

Mark Savage
Music correspondent
 Image source, XL Recordings
Image source, XL RecordingsThe fourth album by Dublin’s Fontaines DC sees the quintet take their scratchy, sinister sound and…

Two leading experts in the field of carbon capture and sequestration (CCS) — Howard J. Herzog, a senior research engineer in the MIT Energy Initiative, and Niall Mac Dowell, a professor in energy systems engineering at Imperial College London — explore methods for removing carbon dioxide already in the atmosphere in their new book, “Carbon Removal.” Published in October, the book is part of the Essential Knowledge series from the MIT Press, which consists of volumes “synthesizing specialized subject matter for nonspecialists” and includes Herzog’s 2018 book, “Carbon Capture.”
Burning fossil fuels, as well as other human activities, cause the release of carbon dioxide (CO2) into the atmosphere, where it acts like a blanket that warms the Earth, resulting in climate change. Much attention has focused on mitigation technologies that reduce emissions, but in their book, Herzog and Mac Dowell have turned their attention to “carbon dioxide removal” (CDR), an approach that removes carbon already present in the atmosphere.
In this new volume, the authors explain how CO2 naturally moves into and out of the atmosphere and present a brief history of carbon removal as a concept for dealing with climate change. They also describe the full range of “pathways” that have been proposed for removing CO2 from the atmosphere. Those pathways include engineered systems designed for “direct air capture” (DAC), as well as various “nature-based” approaches that call for planting trees or taking steps to enhance removal by biomass or the oceans. The book offers easily accessible explanations of the fundamental science and engineering behind each approach.
The authors compare the “quality” of the different pathways based on the following metrics:
Accounting. For public acceptance of any carbon-removal strategy, the authors note, the developers need to get the accounting right — and that’s not always easy. “If you’re going to spend money to get CO2 out of the atmosphere, you want to get paid for doing it,” notes Herzog. It can be tricky to measure how much you have removed, because there’s a lot of CO2 going in and out of the atmosphere all the time. Also, if your approach involves, say, burning fossil fuels, you must subtract the amount of CO2 that’s emitted from the total amount you claim to have removed. Then there’s the timing of the removal. With a DAC device, the removal happens right now, and the removed CO2 can be measured. “But if I plant a tree, it’s going to remove CO2 for decades. Is that equivalent to removing it right now?” Herzog queries. How to take that factor into account hasn’t yet been resolved.
Permanence. Different approaches keep the CO2 out of the atmosphere for different durations of time. How long is long enough? As the authors explain, this is one of the biggest issues, especially with nature-based solutions, where events such as wildfires or pestilence or land-use changes can release the stored CO2 back into the atmosphere. How do we deal with that?
Cost. Cost is another key factor. Using a DAC device to remove CO2 costs far more than planting trees, but it yields immediate removal of a measurable amount of CO2 that can then be locked away forever. How does one monetize that trade-off?
Additionality. “You’re doing this project, but would what you’re doing have been done anyway?” asks Herzog. “Is your effort additional to business as usual?” This question comes into play with many of the nature-based approaches involving trees, soils, and so on.
Permitting and governance. These issues are especially important — and complicated — with approaches that involve doing things in the ocean. In addition, Herzog points out that some CCS projects could also achieve carbon removal, but they would have a hard time getting permits to build the pipelines and other needed infrastructure.
The authors conclude that none of the CDR strategies now being proposed is a clear winner on all the metrics. However, they stress that carbon removal has the potential to play an important role in meeting our climate change goals — not by replacing our emissions-reduction efforts, but rather by supplementing them. However, as Herzog and Mac Dowell make clear in their book, many challenges must be addressed to move CDR from today’s speculation to deployment at scale, and the book supports the wider discussion about how to move forward. Indeed, the authors have fulfilled their stated goal: “to provide an objective analysis of the opportunities and challenges for CDR and to separate myth from reality.”