Eligible Pakistanis can submit passport details and facial biometrics via Australia’s free Immi App
Australian High Commissioner, Timothy Kane said this app is a major step forward in making the Australian visa process easier and more…
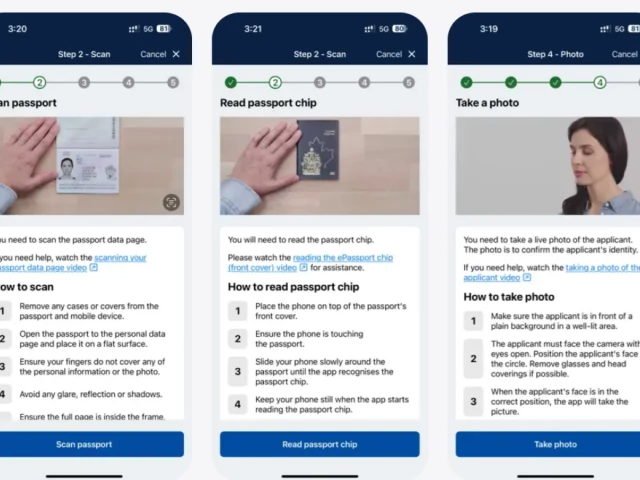
Eligible Pakistanis can submit passport details and facial biometrics via Australia’s free Immi App
Australian High Commissioner, Timothy Kane said this app is a major step forward in making the Australian visa process easier and more…