A company that sells spyware that monitors individuals on parole and probation had its data leaked to a cybercrime forum this week. The leak, according to an analysis by Straight Arrow News, exposed highly sensitive information regarding employees of the corrections system and those under court-ordered supervision.
The affected company, RemoteCOM, describes itself as “the premier computer, smartphone and tablet monitoring service for the management of pretrial, probation and parole clients.” The data indicates that RemoteCOM’s services are used by parole and probation officers in 49 states.
Download the SAN app today to stay up-to-date with Unbiased. Straight Facts™.
Point phone camera here
A training manual in the leaked data for RemoteCOM’s software, known as SCOUT, says the spyware can be used to track everyone from sex offenders, sex traffickers and stalkers to terrorists, hackers and gang members.

SCOUT monitors keystrokes, emails, chats, location data and other on-device activities. The software can also capture screenshots, block access to websites and send alerts when certain keywords are typed by an offender.
The hacker responsible for the breach, known online as “wikkid,” told SAN the intrusion was “one of the easiest” they’d ever carried out. SAN alerted RemoteCOM to the data breach in a phone call on Thursday, but the company did not respond.
The data includes the names and addresses of probation agencies using RemoteCOM’s software as well as contact information, such as email addresses and phone numbers, for more than 800 probation supervisors. The names, email addresses and phone numbers of more than 80 former and current RemoteCOM employees were also exposed.
Eva Galperin, director of security at the Electronic Frontier Foundation, told SAN that the leak is an example of how monitoring technology can make sensitive data more vulnerable to hackers.
“This is quite the oversight for a company with sensitive government contracts that is entrusted with extremely personal and private data, not just about parolees but about government workers,” Galperin said.
Personal information exposed
A file titled “officers” in the leak contains 6,896 entries for people who work in the criminal-justice system and who currently or have previously used RemoteCOM’s services. Each entry shows the person’s name, phone number, work address, email addresses, unique ID and job title.
Another file titled “clients” contains identifying information on nearly 14,000 individuals who have been monitored by SCOUT. The offenders’ names, email addresses, IP addresses, home addresses and phone numbers are listed next to the names and email addresses of their probation officers.
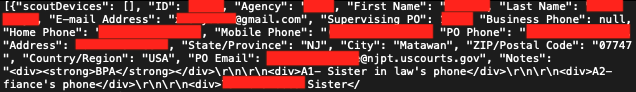
In one example, an entry detailing an offender notes that SCOUT had been installed on phones belonging to the person’s sister-in-law and fiancé. A discussion about SCOUT in a Reddit-based sex offender support group says the spyware “has to be installed on every device” that an offender has “reasonable access to.”
“Your [probation officer] will tell them how many devices it needs to be installed on,” one user wrote. “You’ll then call RemoteCom and set up an appointment to have them remotely install it.”
An informational handout in the leak says offenders are charged $50 for every computer SCOUT must be installed on, while phone installations cost $30. Once installed, offenders are charged a $35 monitoring fee every month.
The hacked data also highlights whether an individual being monitored has been charged with sex offenses, weapons, terrorism, narcotics, stalking, domestic violence, sex trafficking, fraud, violence or hacking, among other charges. Offenders believed to be “tech savvy” are even given a specific label.
Alerts give insight
More than 380,000 alerts sent to probation officers about activities on offenders’ devices offer further insight into SCOUT’s abilities. One probation officer received an alert that “Notable Information” had been detected on the computer of an offender listed as having terrorism and weapons charges.
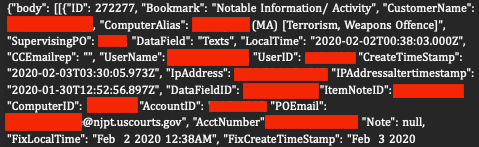
In others examples, alerts announce the purported discovery of potential parole and probation violations. The data does not provide details on what specifically caused the alerts.
A small sample of unpublished data provided to SAN by the hacker also appears to show keywords flagged by SCOUT. In one instance, an offender apparently triggered an alert after typing “Nazi,” while another set off the system by typing “sex.”
contributed to this report.
