Unless you’ve been hiding under a rock, security and privacy are two very hot topics. There’s a good reason for that: because everyone seems to be out for your data and/or information. Companies want to fingerprint you (so they can better create targeted ads), and bad actors want to take anything they can that might help them in the battle to hijack your identity or make off with your bank account information.
No one wants that.
Part of the reason this has become so rampant today is browser insecurity. Most modern web browsers might make life a bit easier for you (especially with the advent of agentic options), but in the process, they also make things less secure. There are just a few browsers out there that can strike a perfect balance between user-friendliness and security. For example, you could use Brave, which does a fairly good job of handling both of these aspects. Even then, however, you could find yourself vulnerable to either privacy or security issues.
Beyond that, most other browsers are not nearly as secure.
So, what do you do when you want the utmost in security while browsing that information superhighway (pardon me for the whimsical turn of title)?
You turn to Tor.
What Is Tor?
For those of you who already know what Tor is, feel free to skip to the next section. Those who are unfamiliar with this browser, read on.
Tor is a special web browser that uses the Tor Network (also known as the Onion Network).
Say what?
The Tor network is a volunteer-operated, open source global overlay network that ensures anonymous communication and online privacy. Tor Network works by “onion routing” (hence the name), which encrypts data in multiple layers and sends it through a random circuit of at least three relays (aka nodes) before it ever reaches its destination. When the data reaches a node, it decrypts one layer of the data to discern the next node in the path, all the while never knowing what the originating IP address or the final destination is. By doing this, your data is truly anonymous.
And anonymity of data packets should be the goal.
You might think this sounds far too complicated to use, but it’s actually not. I remember when I first started using Tor Browser; it was much more complicated and far slower than using a standard browser. These days, the tool is much easier and faster.
But that doesn’t mean you should simply install the basic Tor Browser and have at it. On Linux, there’s a much easier method to this madness, and it’s called Tor Launcher.
What Is Tor Launcher?
Tor Launcher (or Tor Browser Launcher) is a user-friendly tool that makes installing and using Tor Browser considerably easier, which means you don’t have to work so hard to get your data anonymized or encrypted. With Tor Launcher, you get:
- The most recent version of Tor Browser for your language and system architecture.
- Automatic updating of Tor Browser.
- Verification of the Tor Browser GnuPG signature.
- AppArmour profiles to ensure a Tor compromise isn’t nearly as bad as it could be.
- A Tor Browser launcher in your desktop menu.
- A fun modem sound (optional) for when you open Tor Brower.
You might be wondering why the developers included the modem sound. Well, if there’s one thing about Tor Browser that some users complain about, it’s the speed. Because of the way Tor Browser works, it’s noticeably slower than other browsers. Because of that, the developers added the optional modem sound as a throwback to dial-up.
Fun times, that was.
Any time I need to install Tor Browser on Linux, I always use Tor Launcher, simply because it makes everything easier.
How To Install Tor Launcher
The good news is that Tor Launcher has a Flatpak installer, so it’s available to any distribution that uses Flatpak apps. Since most Linux distributions support Flatpak, you can be certain that the installation of Tor Launcher will be simple.
How simple? Let me show you.
The first thing you need to do is make sure your distribution supports Flatpak. To do this, open your distribution’s software center and search for Flatpak. If you see an entry for the universal package manager, install it. If you don’t find it in your distribution’s app store, you could always install it with one of the following commands:
|
|
Debian–based distributions: sudo apt–get install flatpak –y Fedora–based distributions: sudo dns install flatpak –y Arch–based distributions: sudo pacman –S flatpak –y |
Once the installation is completed, reboot your system so Flatpak is available globally.
With Flatpak installed, it’s now time to add Tor Launcher.
For this, issue the command:
|
|
flatpak install flathub org.torproject.torbrowser–launcher |
If, after the installation, you do not find a Tor Browser entry in your desktop menu, you’ll need to log out and log back in so the changes take effect.
You now have Tor Launcher installed and ready to use.
Using Tor Launcher
When you open Tor Launcher, it automatically opens Tor Browser and establishes a connection to the Tor Network (Figure 1). By doing this, you don’t have to worry about remembering to connect to the Tor Network after you open Tor Browser. Essentially, Tor Launcher does everything for you.
Figure 1. Tor Browser is open and automatically connected to the Tor Network.
At any time, you can also reset your identity within Tor Browser. Essentially, this closes all tabs and windows, clears all private information (such as cookies and browsing history) and establishes new Tor circuits for the connection. By resetting your identity, you don’t have to worry about your Tor session having any browsing activity from previous sessions linked to the current activity.
To reset your identity, all you have to do is click the little broom icon to the right of the address bar (Figure 2).
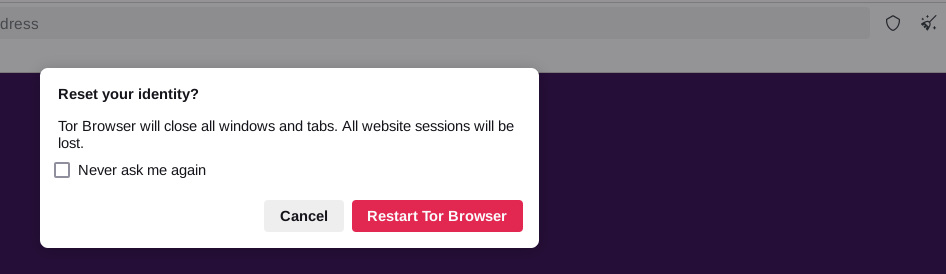
Figure 2. Resetting your Tor Browser identity.
Now that you have the hang of running Tor Browser with the Tor Launcher on Linux, you’ll find the experience to be quite easier (but still slow).
YOUTUBE.COM/THENEWSTACK
Tech moves fast, don’t miss an episode. Subscribe to our YouTube
channel to stream all our podcasts, interviews, demos, and more.

