Your router is the gateway between your Local Area Network (LAN) and the wild west of the Internet, and it should be your first line of defense for your privacy. But routers, even custom ones running OPNsense, are set up to get you online, not for your privacy. Even going through a basic checklist of security fixes will get your network more secure, but it only goes part of the way towards making your browsing more private.
For that, there are a few things I like to change every time I set up a new router. The biggest of these is to set up a self-hosted DNS server that enables encrypted DNS. Otherwise, your ISP (or Google) can see what your DNS requests are and use that data for targeted advertising, and nobody likes the thought of that. Some overlap with good security measures, and there are also things you can do on your devices to protect your privacy, like turning off telemetry and using a privacy-focused browser.
Related
6 overlooked router settings that can improve your network security
You can make your home network much more secure with a few changes.
4
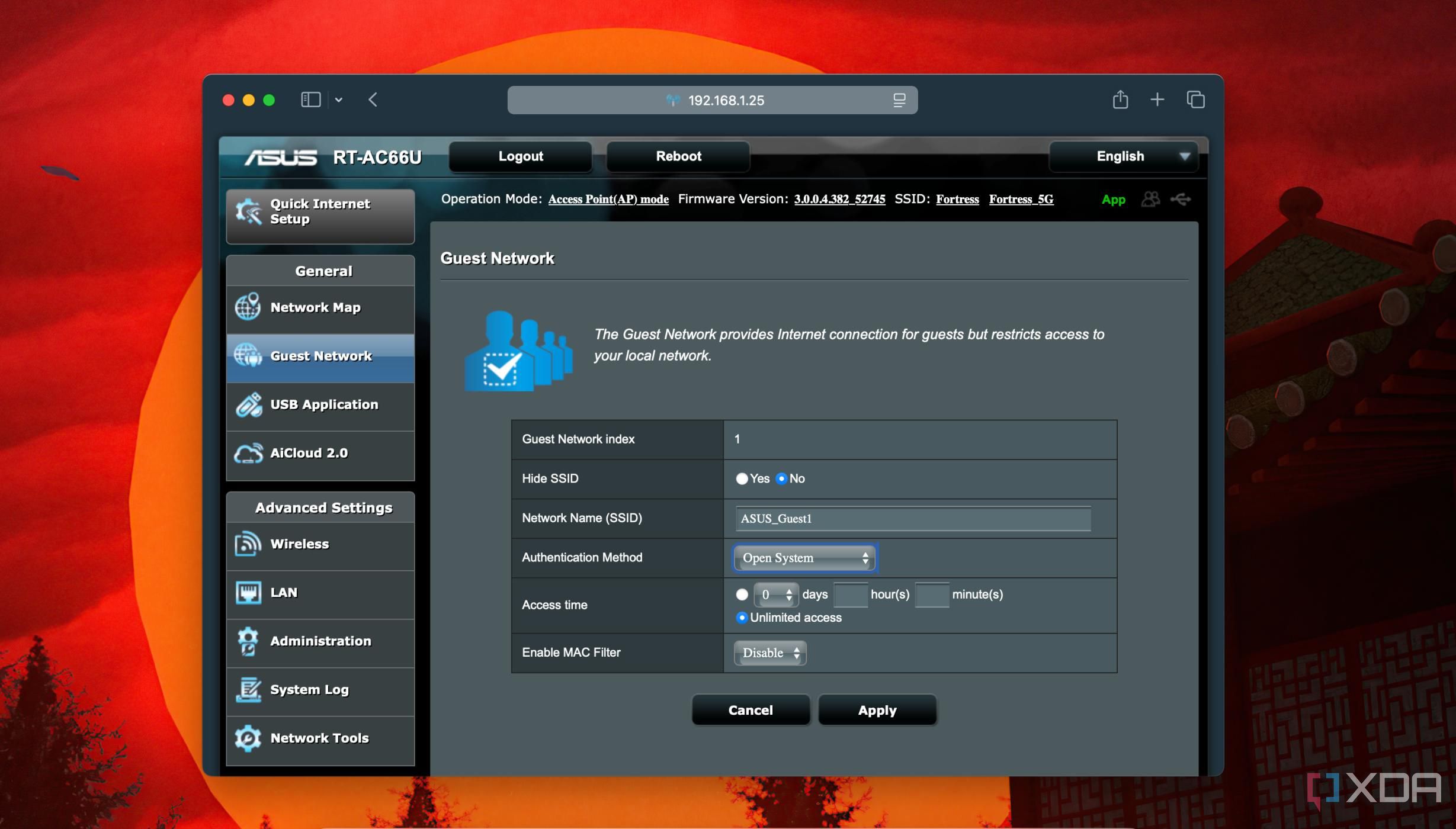
I host my own DNS server
Privacy by design with no ISP snooping
It should come as no surprise that your ISP is spying on you, as is Google, MSN, and probably every website you visit. It’s concerning, to say the least, how easily our private information is being used for targeted advertising and other things. However, by knowing that, you can plan countermeasures to minimize the amount of identifying information leaked while you use the internet.
That’s why the first thing I change on any router is the DNS servers, specifically to a DNS server that I’m self-hosting. This could be Unbound, Technitium, or Pi-hole set up with DNSCrypt, but it’s non-negotiable because encrypted DNS requests stop the ISP from snooping. If you have an Eero mesh, Eero Secure also gives you encrypted DNS records (that filter all outgoing DNS requests, even those not pointed at the Eero DNS server), but you have to be okay with Amazon being in charge of that, and that’s a dealbreaker for many.
You don’t have to use DNSCrypt; DNS-over-TLS and DNS-over-HTTPS also work if your DNS server supports them. You’ll also want DNSSEC support so your DNS resolver can trust the results it gets back. Without it being encrypted, everyone on your local Wi-Fi network, your ISP, and transit providers can all see the data contained in your DNS queries and responses, which include the UDP port used, the IP addresses and URLs involved, if any HTTPS traffic happened (indicated visiting other pages on that URL), and more.
Unencrypted DNS queries can be hijacked, which is often done by ISPs to redirect users to advertising pages or block content they don’t want them to see. Any firewalls along the route could also intercept, block, or modify DNS traffic, so keeping it encrypted with DoT or DoH is essential for privacy on the web. Services like Cloudflare DNS and Quad9 support encryption while having no-logging policies, so your identity is kept private. And since you’re running the DNS resolver, you can block known trackers, malware domains, and even ads.
Related
Forget about Pi-hole, I switched to this more powerful self-hosted alternative
Technitium is my new bestie.
3
Disable UPnP, NAT-PMP, and WPS
These vulnerable features could mean your network is no longer private
I don’t know about you, but privacy to me also means not leaving the proverbial door open for attackers to look around. Unfortunately, many consumer routers have features enabled by default that make it trivial for anyone to invade the privacy of your home network, and those are also on my list of things to change.
Thankfully, Wi-Fi Protected Setup (WPS) doesn’t exist on most newer devices. However, it’s still available and makes an easy way for an attacker to crack your Wi-Fi password, because a six-digit PIN code is several orders of magnitude easier than a long password. Turn that off, then turn off UPnP and NAT-PMP (if your router supports it), because those make it easy for any IoT device inside your network that might have been pulled into a botnet by malware able to open ports to the internet.

Related
4 reasons you should consider disabling UPnP in your router
You probably don’t need it anymore, and it’s a security nightmare.

Related
4 reasons you should disable NAT-PMP on your router right now
This Apple-centric alternative to UPnP is no longer necessary.

Related
4 reasons you should turn off Wi-Fi Protected Setup (WPS) right now
WPS used to be a quick way to pair Wi-Fi devices, but you shouldn’t use it anymore.
2
Isolate the guest network
It shouldn’t be able to talk to the rest of my network or devices
Even if you aren’t running a VLAN for your IoT devices so they can’t access the data on your main computers, you should still be running a guest network for any visitors who may want to use your internet. It’s part of being a good host, but you don’t have to sacrifice your privacy by giving out the password to your Wi-Fi network.
For this to be truly effective, you’ll want to enable Client or AP Isolation (depending on how your router manufacturer names it), so that any of these guest devices won’t be able to see your devices or connect to each other. The guest network is simply so they’re not running down cellular data caps while at your home, and you can add bandwidth limits to ensure all your guests get passable service, and remove the network once everyone goes home, so they can’t connect to your network unless you know they’re using it.
Related
6 tips to securely share guest Wi-Fi with friends
Make guest access easy backed by robust security
1
Turn off legacy device support
If it’s insecure, I don’t want it on my network
Wi-Fi has evolved substantially since its inception, and your home network isn’t private if you still have legacy devices connected. These legacy protocols include WEP, WPA, and TKIP, and they shouldn’t be used on your home router. The best Wi-Fi security you can use is WPA3 with AES, which you should look for when you next plan a router purchase.
However, it’s also important to look for any devices you may have that cannot use WPA3. Anything that uses WEP or TKIP encryption lulls you into a false sense of security because Wi-Fi cracking tools can brute-force these in minutes. WPA3 includes features that eliminate the way attackers can figure out passwords based on handshake data or force devices off the network to continually get the handshake data they need.
Enabling WPA3 on any new Wi-Fi router is one of the first things I’ll do, and it’s easy to handle because it’s done at the same time as adding Wi-Fi passwords and which wireless bands are being used. I’ll also turn off support for 802.11a/b/g/n because almost every device on my network uses Wi-Fi 5 or newer, and I’ve replaced most of the devices that only use 2.4GHz. That doesn’t make it more private, but it does show me which older devices I really should replace, as they’re often using insecure methods that slow down the rest of my network.

Related
7 systems running on legacy tech in 2024
It’s slightly sobering how many super-critical industries or systems still run on older technology.
These steps are just the start of keeping your information private online
Keeping your data and network private is a never-ending task as companies and individuals create new ways to access our data. It’s essential to know the why behind turning off default settings or installing new software, as the tools change, but the basic tenets don’t. Encryption is good, but it needs to be used in every part of the chain, from web browsers to DNS requests, and every network segment in between. Physical privacy methods also have digital counterparts, and finding the ones that work for you is more important than using the most popular options. And above all, regular check-ins to see if new digital fingerprinting methods have been developed and how to outwit them.