Blood clots don’t always appear where you expect them. Beyond the legs and lungs, blood clots can also occur in less common areas of the body. These unusual clot locations can lead to delayed treatment,…
Author: admin
-

CSULB art grads illustrate the storyboards that bring Hollywood blockbusters to life
As they discovered their love of storytelling through hand-drawn illustrations, or found their unique style through animated images, Cal State Long Beach students and alumni have excelled as storyboard artists, working for some of the…
Continue Reading
-

Tiny RNA molecules in sperm, big impact on baby health
Key takeaways
- The study pinpoints a specific sperm-enriched RNA that is actively packaged during sperm maturation and delivered to the embryo at fertilization, where it helps regulate early gene activity critical for cell division and…
Continue Reading
-
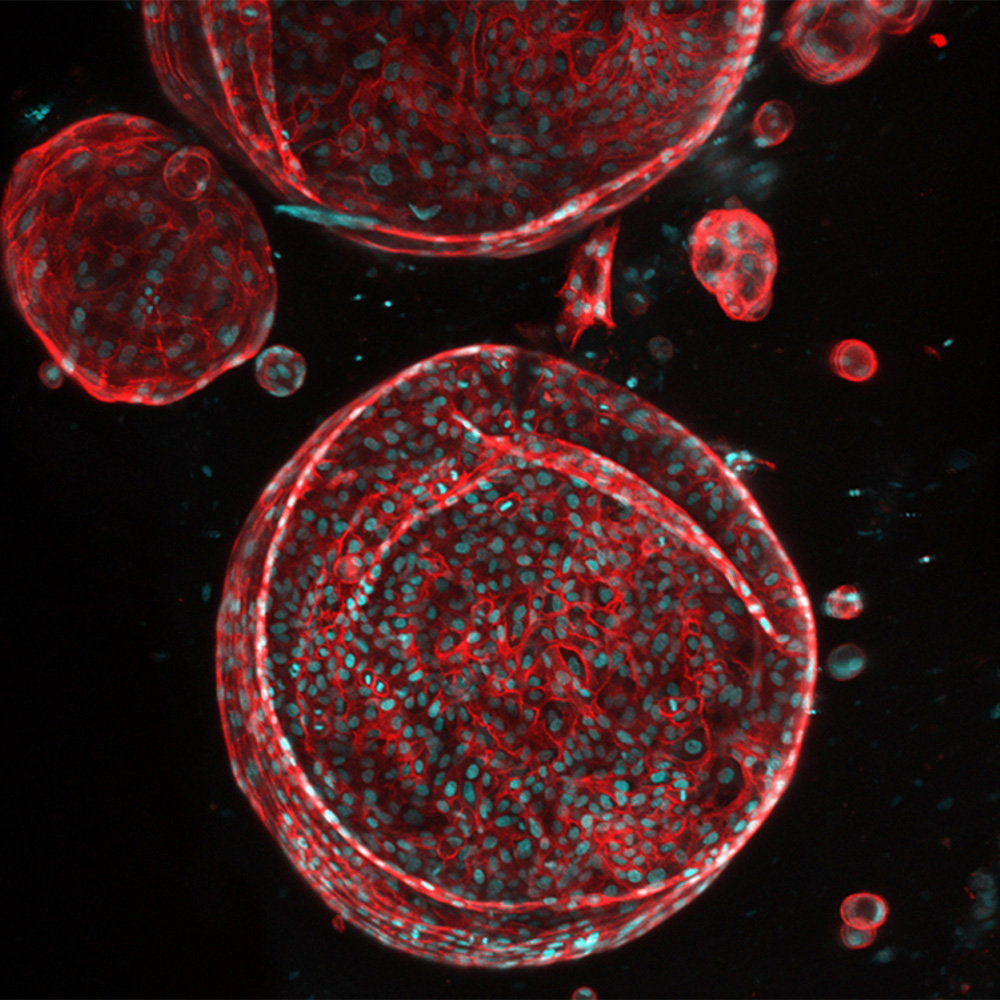
UTSW receives ARPA-H award to create functioning artificial liver: Newsroom
Patient biopsy-derived liver organoids can serve as building blocks for biofabrication of a personalized, patient-specific whole liver. This image shows liver organoids generated from a patient liver biopsy with alcoholic…
Continue Reading
-

MTG Arena Announcements – January 12, 2026
In this edition:
Lorwyn Eclipsed Card Previews
0004_MTGECL_Main: Ajani, Outland Chaperone
0061a_MTGECL_Main: Oko, Lorwyn Liege
Want to see all the cards in Lorwyn Eclipsed before it comes to MTG Arena on January 20? We have…
Continue Reading
-

Tiny Mars’ big impact on Earth’s climate | UCR News
At half the size of Earth and one-tenth its mass, Mars is a featherweight as far as planets go. And yet, new research reveals the extent to which Mars is quietly tugging on Earth’s orbit and shaping the cycles that drive long-term climate…
Continue Reading
-

Tributes paid to ‘extraordinary musician’
Catherine LystBBC Scotland News
 The Wallace Collection
The Wallace CollectionJohn Wallace was made a CBE in 2011 and was awarded a Queen’s Medal for Music in 2021 Tributes have been paid to “extraordinary musician” Prof John Wallace who has died at the age of 76.
Wallace,…
Continue Reading
-

John Wallace: Tributes paid to 'extraordinary musician' – BBC
- John Wallace: Tributes paid to ‘extraordinary musician’ BBC
- John Wallace, trumpeter who accompanied Kiri te Kanawa at the wedding of Prince Charles and Diana The Telegraph
- Sad passing of top trumpet, 76 Slipped Disc
- Conservatoire mourns loss of…
Continue Reading
-

Trump to meet with Venezuelan opposition leader Machado on Thursday | US-Venezuela Tensions News
The Venezuelan opposition figure has been largely frozen out of US discussions over the country’s future.
Published On 12 Jan 2026
United States President Donald Trump will meet with…
Continue Reading
-

Vigil for Renee Good and Other Victims of ICE Brutality
We will gather on Tuesday, 13 January at 6pm to honour the life of Renee Good and all those others who have been victims of ICE brutality. Her murder, along with the deaths of others at the hands of Immigration and Customs…
Continue Reading