[Barcelona, Spain, March 2, 2026] At Huawei Product & Solution Launch during MWC Barcelona 2026, George Gao, President of Huawei Cloud Core Network Product Line, unveiled the AgenticCore solution. Designed for AI-centric networks in the agent era, AgenticCore helps operators modernize and strengthen their main services—voice, mobile Internet, and home broadband—and accelerate the evolution toward an agent network featuring terminal-network-business synergy.
George Gao delivering a keynote speech
As agent capabilities rapidly expand across terminals and applications, AI is driving the upgrade of operators’ essential services to better meet the differentiated, personalized experience requirements of individuals, families, and enterprises.
AgenticCore supports this transformation by introducing a more intelligent, user-centric service model. It builds user-centric memory, and interprets both B2C and B2H service intent. This helps operators enrich user experience. Looking ahead to a future with hundreds of billions of interconnected agents, AgenticCore provides skill-based routing to ensure efficient agent communication, while strengthening service awareness and agent connectivity to support an agent network with terminal-network-business synergy.
“Huawei is committed to supporting operators in their service transformation,” said George Gao. “AgenticCore provides three service-enabling solutions, two terminal-network-business synergy capabilities, and one intelligent infrastructure for efficient cross-domain and cross-ecosystem collaboration between agents.”
Three Service-Enabling Solutions to Reshape Operators’ Main Services
- AI Calling is the industry’s first AI noise cancellation solution for all generations of mobile communication in all scenarios, making every call crystal-clear. It enables interactive calls to eliminate speech communication barriers and handle multiple tasks through just one call.
- The Intelligent Personalized Experience (IPE) solution differentiates experiences by user or service. This helps operators pivot from traffic monetization to experience monetization.
- The AI home hub provides proactive, emotional services. It can deliver emotional support for the elderly, and smart learning assistance for children.
Two Terminal-Network-Business Synergy Capabilities to Enhance Service Experience
- Artificial Intelligence Service Function (AISF): provides user-centric service agents to integrate B2C and B2H services. This helps operators improve their primary service experience.
- Agent Communication Network (ACN): The agent-based routing architecture enables terminal-network-business synergy across various domains and ecosystems. This allows operators to flexibly expand AI services and develop robust network services based on this architecture.
Intelligent Infrastructure Ready in Advance, Facilitating Smooth Network Evolution
The intelligent infrastructure gets ready in advance, offering diverse computing power, terabit-level inference bandwidth, and agent-based autonomous troubleshooting. It lays a solid foundation for AgenticCore evolution.
George Gao stated that AgenticCore embodies the pivot towards future agent communication networks. Huawei will collaborate with operators and industry partners to help operators reshape their main services, and accelerate the evolution to terminal-network-business synergy with AI service enablement, agent communication, and ready intelligent infrastructure.
MWC Barcelona 2026 will be held from March 2 to March 5 in Barcelona, Spain. During the event, Huawei will showcase its latest products and solutions at stand 1H50 in Fira Gran Via Hall 1.
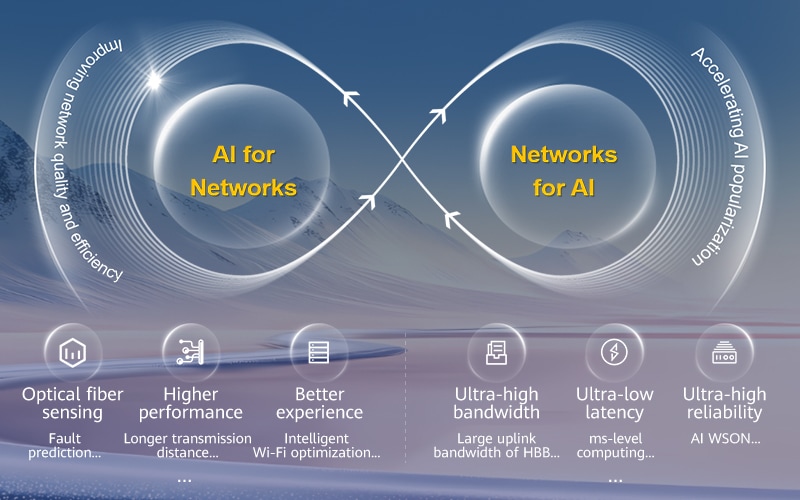
The era of agentic networks is now approaching fast, and the commercial adoption of 5G-A at scale is gaining speed. Huawei is actively working with carriers and partners around the world to unleash the full potential of 5G-A and pave the way for the evolution to 6G. We are also creating AI-Centric Network solutions to enable intelligent services, networks, and network elements (NEs), speeding up the large-scale deployment of level-4 autonomous networks (AN L4), and using AI to upgrade our core business. Together with other industry players, we will create leading value-driven networks and AI computing backbones for a fully intelligent future.
For more information, please visit: https://carrier.huawei.com/en/minisite/events/mwc2026/