For those who missed out on the past few years of ‘smart home’ gadgets, the Logitech POP buttons were introduced in 2018 as a way to control smart home devices using these buttons and a central hub. After a few years of…
Category: 4. Technology
-
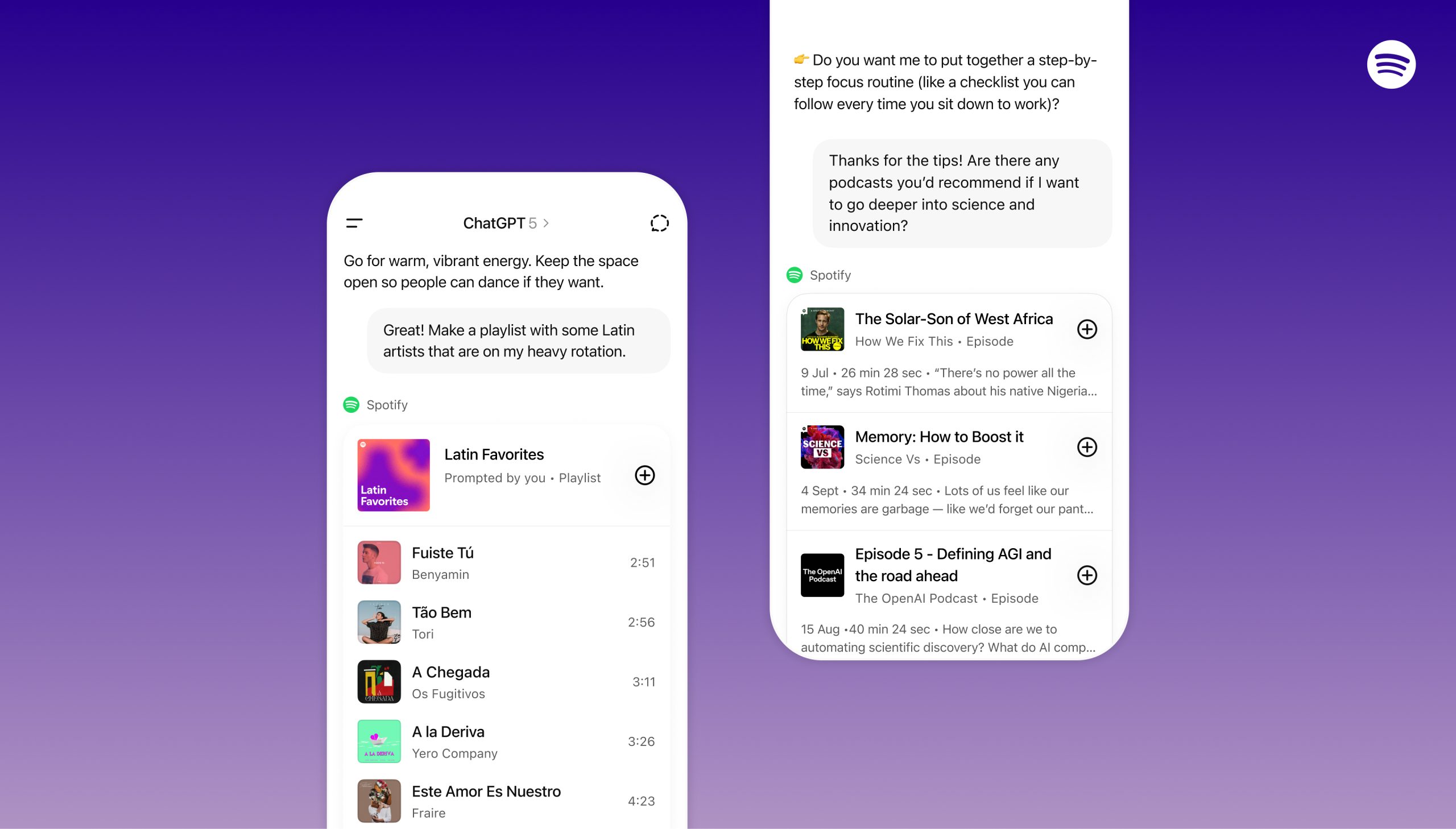
Introducing Spotify in ChatGPT — Spotify
Spotify is everywhere you listen (and watch): in the car, on your TV, and even while gaming — with integrations across more than 2,000 devices. Every listener’s journey is unique;…
Continue Reading
-

Apple’s AirPods Pro 2 Are Teenager-Approved and Now Under $200 for Prime Day
Amazon has deals on all sorts right now, thanks to the October Prime Day event, which means that you can currently get your hands on the excellent Apple AirPods Pro 2 for $199, which is a hefty 20% off the normal price. But Prime Day is ending on…
Continue Reading

