- PUBG mobile 3.9 update brings Transformers mode, now available for download ARY News
- PUBG Mobile KR 3.9 update with new Transformers mode now available for download Moneycontrol
- BGMI 3.9 update release timeline, features and everything else we know so far digit.in
- Optimus and Megatron roll out! — PUBG Mobile launches major new patch EdexLive
- PUBG Mobile Update 3.9 Release Date FreeJobAlert.Com
Category: 4. Technology
-
PUBG mobile 3.9 update brings Transformers mode, now available for download – ARY News
-

Microsoft Patches ‘Wormable’ Critical Flaw, Discloses ‘Whopping’ Number Of Bug Fixes
The 130 CVEs (Common Vulnerabilities and Exposures) disclosed in Microsoft’s monthly release of security fixes includes a remote code execution flaw that ‘definitely’ should be prioritized for patching, writes Trend Micro’s Dustin Childs.
The huge quantity of CVEs (Common Vulnerabilities and Exposures) disclosed by Microsoft Tuesday includes a critical-severity remote code execution flaw that should be given a high priority for patching, according to a Trend Micro researcher.
The flaws received patches as part of Microsoft’s monthly release of software bug fixes, unofficially known as “Patch Tuesday.”
[Related: 5 Things To Know On The SafePay Ransomware Group]
Microsoft released fixes for a total of 130 CVEs on Tuesday, a “whopping” number of patches for a single month, wrote Dustin Childs, head of threat awareness for Trend Micro’s Zero Day Initiative, in a blog post.
As usual, the patches address vulnerabilities that affect numerous Microsoft product categories including Windows, Office, Azure, .NET, Visual Studio, Windows BitLocker, Windows Hyper-V and Microsoft Edge.
Among the highest-risk flaws is a Windows remote code execution vulnerability (tracked at CVE-2025-47981) that “many will be talking about” in the security community for a number of reasons, Childs wrote in the post.
That’s because the flaw “allows remote, unauthenticated attackers to execute code simply by sending a malicious message to an affected system,” he wrote. “Since there’s no user interaction, and since the code executes with elevated privileges, this bug falls into the wormable class of bugs.”
Additionally, Microsoft “gives this [flaw] its highest exploitability index rating, which means they expect attacks within 30 days,” Childs wrote. “Definitely test and deploy these patches quickly.”
The vulnerability has received a severity rating of 9.8 out of 10.0.
In total, 10 of the newly disclosed vulnerabilities patched in the software updates Tuesday are rated as “critical” issues in terms of severity, he noted.
Other critical vulnerabilities disclosed Tuesday include remote code execution flaws affecting Microsoft Office, SharePoint and SQL Server.
Those flaws include a SharePoint remote code execution vulnerability (tracked at CVE-2025-49704) with a severity rating of 8.8 of out 10.0, as well as a SQL Server remote code execution vulnerability (tracked at CVE-2025-49717) with a severity rating of 8.5 out of 10.0.
Continue Reading
-

Browser hijacking campaign infects 2.3M Chrome, Edge users • The Register
A Chrome and Edge extension with more than 100,000 downloads that displays Google’s verified badge does what it purports to do: It delivers a color picker to users. Unfortunately, it also hijacks every browser session, tracks activities across websites, and backdoors victims’ web browsers, according to Koi Security researchers.
Color pickers let users select any color from a website and copy it into a clipboard for later use – helpful for designing apps, websites, and the like. This particular extension from Geco is still available for download via both Microsoft’s and Google’s respective stores at press time. Neither company responded to The Register‘s inquiries, but we will update this story if that changes.
The Geco extension has more than 800 reviews on the Chrome Web Store, 4.2 stars (out of 5), and “featured” placement. Microsoft’s Edge Add-ons shows similarly glowing write-ups from its 1,000-plus users, and it looks like a perfectly safe extension.
“This isn’t some obvious scam extension thrown together in a weekend,” said Koi Security analyst Idan Dardikman in a Tuesday blog. “This is a carefully crafted Trojan horse.”
The Register also reached out to the developer for comment but did not receive a response.
The Geco color picker, according to Koi Security, is “just the tip of the iceberg,” and part of a much larger browser-hijacking campaign dubbed RedDirection. The campaign consists of 18 malicious extensions spanning both Chrome and Edge stores that all share the same snooping capabilities. All 18 extensions are listed at the bottom of this story.
“Combined, these eighteen extensions have infected over 2.3 million users across both browsers, creating one of the largest browser hijacking operations we’ve documented,” Dardikman wrote.
The extensions offer all sorts of capabilities: emoji keyboards, weather forecasts, video speed controllers, VPN proxies for Discord and TikTok, dark themes, volume boosters, and YouTube unblockers (useful if your employer, school, or government blocks the popular video site). But in addition to providing these legitimate functions, they secretly surveil users’ web browsing activity, capturing URLs, sending this info to a remote attacker-controlled server along with the victim’s unique tracking ID, and even redirecting people’s browsers if instructed, according to the researchers.
What makes this even sneakier — and likely explains the Google verified badge — is that these extensions weren’t laced with malware from the start.
According to Dardikman, the code started out clean and sometimes remained that way for years before the malware was introduced during version updates. “Due to how Google and Microsoft handle browser extension updates, these malicious versions auto-installed silently for over 2.3 million users across both platforms, most of whom never clicked anything,” he said.
If you’ve installed any of the extensions listed below, uninstall now, clear your browser data, and keep an eye on your accounts for any suspicious activity.
Extension IDs
Chrome:
- kgmeffmlnkfnjpgmdndccklfigfhajen — [Emoji keyboard online — copy&past your emoji.]
- dpdibkjjgbaadnnjhkmmnenkmbnhpobj — [Free Weather Forecast]
- gaiceihehajjahakcglkhmdbbdclbnlf — [Video Speed Controller — Video manager]
- mlgbkfnjdmaoldgagamcnommbbnhfnhf — [Unlock Discord — VPN Proxy to Unblock Discord Anywhere]
- eckokfcjbjbgjifpcbdmengnabecdakp — [Dark Theme — Dark Reader for Chrome]
- mgbhdehiapbjamfgekfpebmhmnmcmemg — [Volume Max — Ultimate Sound Booster]
- cbajickflblmpjodnjoldpiicfmecmif — [Unblock TikTok — Seamless Access with One-Click Proxy]
- pdbfcnhlobhoahcamoefbfodpmklgmjm — [Unlock YouTube VPN]
- eokjikchkppnkdipbiggnmlkahcdkikp — [Color Picker, Eyedropper — Geco colorpick]
- ihbiedpeaicgipncdnnkikeehnjiddck — [Weather]
Edge:
- jjdajogomggcjifnjgkpghcijgkbcjdi — [Unlock TikTok]
- mmcnmppeeghenglmidpmjkaiamcacmgm — [Volume Booster — Increase your sound]
- ojdkklpgpacpicaobnhankbalkkgaafp — [Web Sound Equalizer]
- lodeighbngipjjedfelnboplhgediclp — [Header Value]
- hkjagicdaogfgdifaklcgajmgefjllmd — [Flash Player — games emulator]
- gflkbgebojohihfnnplhbdakoipdbpdm — [Youtube Unblocked]
- kpilmncnoafddjpnbhepaiilgkdcieaf — [SearchGPT — ChatGPT for Search Engine]
- caibdnkmpnjhjdfnomfhijhmebigcelo — [Unlock Discord]
“No phishing. No social engineering. Just trusted extensions with quiet version bumps that turned productivity tools into surveillance malware,” the blog warns. ®
Continue Reading
-
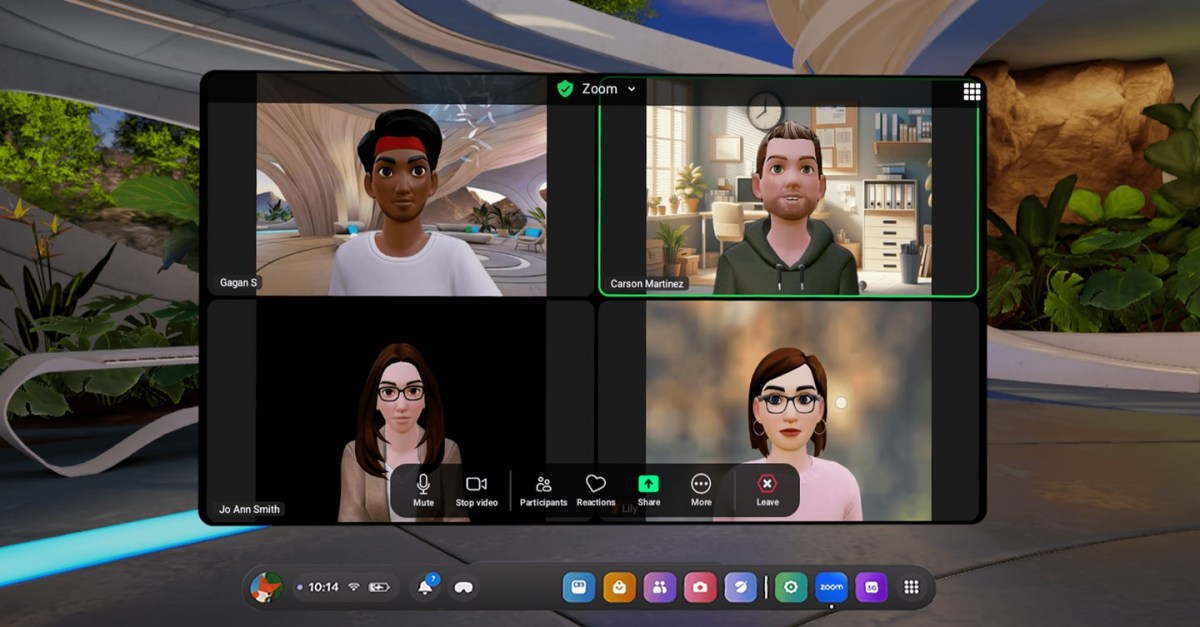
Zoom’s new Meta Quest app encourages taking video calls in VR
Zoom has rolled out a standalone app for Meta Quest headsets. With the app, you can join or host meetings in virtual reality while appearing as your Meta Avatar.
Zoom launched an app for the Quest in 2023, but it was only available through Meta’s Horizon Workspaces app, and users could also only host a meeting if they had a Zoom subscription. Zoom’s new standalone app will work with “any free or paid Zoom license,” according to its listing on Meta’s site. It also supports Meta Quest 3, Quest 3S, Quest Pro, and Quest 2 headsets.
When using Zoom on the Quest, you’ll also see other participants on your call, whether they’re using the service’s desktop, mobile, or web app. Meta notes that you can join meetings using passthrough mode as well, a feature that allows you to see parts of your real-life environment while wearing Meta Quest 3, Quest 3S, and Quest Pro headsets.
Continue Reading
-

Amazon gets the green light to sell the Nintendo Switch 2
It’s a big change following Nintendo removing listings for its products from Amazon starting last year. Bloomberg reported in June that Nintendo pulled the listings because third-party sellers sold games at prices “that undercut Nintendo’s advertised rates.” Nintendo and Amazon pushed back on Bloomberg’s report in statements to the publication but didn’t go into specifics.
If you request an Amazon invite, the product page will show a message saying that “if invited to purchase, you’ll get an email with a link that’s valid for 22 hours. We won’t be able to grant all requests.” I got an email notifying me about my request, too.
The Switch 2 has been a huge hit for Nintendo, becoming the fastest-selling game console of all time since its June 5th launch. If you are still looking for a console and Amazon doesn’t come through, retailers like Walmart and Best Buy have occasional restocks.
Continue Reading
-

Balancing cost and quality of life
A recent study in JAMA Network Open found that although trimodal therapy (TMT) improved quality of life for patients with muscle-invasive bladder cancer, it was not as cost-effective as radical cystectomy.1 However, the immediate implication for clinicians is not to abandon TMT, but to be highly selective about patient choice, according to study author Daniel D. Joyce, MD, MS, assistant professor of urology at Vanderbilt University Medical Center in Nashville, Tennessee. TMT is best suited for patients with very limited disease who can maintain a good quality of life with their bladders, rather than those with extensive cancer or bilateral hydronephrosis. The goal is to improve the value of care by ensuring TMT is used in patients most likely to achieve metastasis-free and overall survival benefits.
Regarding policy changes to reduce TMT costs, Joyce brought up a comparison with the Canadian health care system. In Canada, TMT was found to be the most cost-effective option, with costs around $20,000 USD at 5 years, compared with $70,000 in the US.2 The primary driver of this cost difference in the US is radiation therapy, as chemotherapies are relatively inexpensive.
According to Joyce, policy initiatives should focus on improving the value and efficiency of radiation. This could involve re-evaluating current fee-for-service billing for radiation, which encompasses physician, facility, and per-fraction Current Procedural Terminology codes, to determine whether current expenditures are justified. Moving toward value-based or bundled payment programs for radiation is 1 potential option to promote higher value and efficiency. Additionally, broader societal discussions are needed concerning the density of high-cost technologies like proton beams to encourage efficiency.
REFERENCES
1. Joyce DD, Wymer KM, Graves JA, et al. Cost-effectiveness of trimodal therapy and radical cystectomy for muscle-invasive bladder cancer. JAMA Netw Open. 2025;8(6):e2517056. doi:10.1001/jamanetworkopen.2025.17056
2. Kool R, Yanev I, Hijal T, et al. Trimodal therapy vs. radical cystectomy for muscle-invasive bladder cancer: A Canadian cost-effectiveness analysis. Can Urol Assoc J. 2022;16(6):189-198. doi:10.5489/cuaj.7430
Continue Reading
-

Activision took down Call of Duty game after PC players hacked, says source
Games giant Activision took down “Call of Duty: WWII” due to hackers exploiting a flaw in a specific PC version of the game, which led to several players getting their computers hacked, TechCrunch has learned.
Last week, Activision announced that it brought offline the Microsoft Store version of “Call of Duty: WWII,” a 2017 first-person shooter, as the company was investigating “reports of an issue,” without specifying what the issue was. The company had just launched that version of the game, also available on Game Pass, a subscription service that provides access to several games for a monthly fee.
A person with knowledge of Activision’s response told TechCrunch that the company took the game offline because of the hacks and while it works to patch the issue. TechCrunch is not naming the person as they are not authorized to speak to the press.
Several video game news outlets reported on the story and noted that several players complained on social media that they had been hacked while playing the game. Until now, there had not been a confirmed link between the two events.
“The game is not safe to play on PC right now, there’s an RCE exploit,” a player wrote on Reddit last week, referring to a type of bug known as remote code execution, which allows hackers the ability to plant malware capable of essentially taking control of a victim’s device.
The game for the Microsoft Store and Game Pass remains down at the time of publication, per Activision’s status page.
Activision did not respond to multiple requests for comment.
The game publisher took down only the Microsoft Store and Game Pass version of “Call of Duty: WWII” because they were different versions of the game than listed on Steam, and contained an old flaw that had been patched on other versions of the game, according to two sources with knowledge of the situation.
Contact Us
Do you have more information about these hacks? Or other video game hacks? From a non-work device and network, you can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, or via Telegram and Keybase @lorenzofb, or email.
In the last couple of years, Activision has had to deal with several hacking incidents. In November 2024, a hacker found a flaw in Call of Duty’s anti-cheat system that allowed them to ban thousands of legitimate gamers. Earlier in the year, the company investigated a hacking campaign targeting players with infostealer malware, a type of malicious software designed to steal a victim’s passwords. In 2023, hackers used a self-spreading malware — a computer worm — to hack “Call of Duty: Modern Warfare” players, thanks to an unpatched years-old bug in the game.
In recent times, some video game companies have beefed up their cybersecurity teams, as well as their anti-cheat teams. Activision, however, has gone through several rounds of layoffs in the last few years, some of which have directly affected its cybersecurity teams.
Continue Reading
-

Anatsa mobile malware returns to victimize North American bank customers
The long-running Android banking trojan known as Anatsa recently targeted financial institutions and banking app users in North America, researchers said.
The campaign marks at least the third time the malware has been aimed at mobile banking customers in the United States and Canada, according to Dutch cybersecurity firm ThreatFabric, which has been monitoring Anatsa’s activity since 2020.
Anatsa is capable of stealing banking credentials, logging keystrokes and carrying out fraudulent transactions directly from infected devices using remote-access tools.
Anatsa campaigns typically begin with a developer uploading a legitimate-looking Android app — such as a PDF reader or phone cleaner — to an app store, where it functions normally until it amasses thousands of downloads. At that point, an update injects devices with malicious code that installs Anatsa as a separate application on the device. The code then carries out various malicious activities, depending on the target.
In the recent campaign, the malware was embedded in a seemingly harmless file reader app roughly six weeks after its release. The malicious update was delivered to devices from June 24-30. The app ranked among the top free tools in the U.S. version of the Play Store before it was removed, accumulating more than 50,000 downloads, ThreatFabric said.
That two-stage pattern is familiar, said Randolph Barr, the CISO at application security company Cequence.
“Even savvy users may miss this, since the initial app appears clean and functional,” he said.
Researchers haven’t specified how the hackers promoted the app to achieve a wide reach. It’s also unclear how the threat actors use the stolen data, though possible scenarios include ransomware attacks or selling the information to other cybercriminals on darknet marketplaces.
A key feature of the operation was its expanded list of targets, which included a broader range of mobile banking applications in the United States, ThreatFabric said.
Banking trojans are common tools among cybercriminals, designed to steal sensitive financial information. Their deployment often leads to unauthorized transactions, account takeovers, and significant monetary losses for victims.
“Looking ahead, we’ll likely see more campaigns like this evolve further,” Barr said. “This includes things like AI-personalized malware overlays targeting specific banks or regions, modular payloads downloaded in real time post-install, attempts to bypass MFA [multi-factor authentication] via screen overlays or token theft, and even more abuse of accessibility services and session hijacking.”
Earlier in June, ThreatFabric discovered a new version of the Android banking trojan known as Crocodilus, which is spreading across Europe, South America, and parts of Asia. The malware’s latest variant can insert fake entries into victims’ contact lists, allowing attackers to impersonate trusted sources — such as bank support lines — and trick users into answering fraudulent calls, potentially bypassing fraud prevention systems that flag unknown numbers.
Jonathan Greig contributed to this story.
Get more insights with theRecorded Future
Intelligence Cloud.
Learn more.
Continue Reading
-

These budget Bose-tuned earbuds are 40% off and worth every penny
The Skullcandy Method 360 ANC earbuds were already a steal at their $99 launch price, undercutting their $129.99 MSRP. But this Prime Day, you can snag them for only $75.99 ($54 off). That’s 40% off for earbuds that deliver Bose-tuned sound and premium features without the premium price.
What makes these so special? Skullcandy teamed up with Bose to pack in surprising technology. These earbuds use licensed Bose drivers, acoustic tuning, and even the same ergonomic ear tips and fins found on Bose’s flagship QuietComfort Ultra Earbuds. The result is a secure, fatigue-free fit and impressive noise isolation for the price.
The active noise canceling (ANC) is no slouch. The Method 360 ANC effectively reduces low-frequency rumbles, like engines or air conditioners, by up to 28dB. It also dulls higher-pitched sounds like chatter and keyboard clicks surprisingly well, making commutes, flights, or busy offices much quieter. And if you want to stay aware of your surroundings, the Stay-Aware mode balances ambient sound without overwhelming your music.

The sound signature leans towards heavy bass, which is perfect for EDM and hip-hop fans but doesn’t stop there. Using the Skull-iQ app, you can customize the audio with a 5-band EQ, tweak ANC and transparency levels, and even remap the touch controls. Add Bluetooth multipoint for easy device switching and a low-latency mode for gaming, and you’re looking at a feature-packed set of buds under $80.
Even the case is designed to turn heads. Its cylindrical shape includes a carabiner clip for attaching to your bag or belt loop. The case comes in bold colors like Leopard Print, Lava Red, and Aurora Black. It can take some time to get used to a case that you don’t just shove in your pocket, but once you get the hang of it, it’s a unique design that is practical and stylish.
With up to 8 hours of playback (ANC on) and 32 hours total with the case, the Method 360 ANC offers incredible value for anyone craving Bose-level tech on a budget. Don’t wait too long; Prime Day deals like this won’t stick around forever.
Skullcandy Method 360 ANC with Sound by Bose

Skullcandy Method 360 ANC with Sound by Bose
Comfort • Fit • ANC • App
Big bass, solid ANC, and plenty of features if you can handle the bold design and quirky case.
The Skullcandy Method 360 ANC delivers solid ANC, great comfort, and a feature-packed app, but its booming bass and quirky case design won’t be for everyone. Still, these are good value if you catch them at the right price.
Continue Reading