The Milky Way is a rich and complex environment. We see it as a luminous line stretching across the night sky, composed of innumerable stars.
But that’s just the visible light. Observing the sky in other ways, such as through radio waves,…

The Milky Way is a rich and complex environment. We see it as a luminous line stretching across the night sky, composed of innumerable stars.
But that’s just the visible light. Observing the sky in other ways, such as through radio waves,…
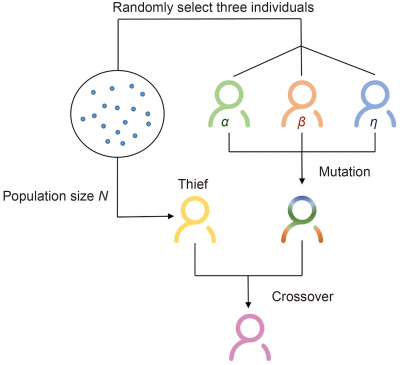
In the field of optimization, metaheuristic algorithms are widely used to solve complex problems in real life and engineering, such as resource allocation, drone path planning, and supply chain management. The dung…

In most animals, stem cells rely on nearby cells to tell them what to do. However, new research from the Stowers Institute for Medical Research shows that flatworm, or planarian, stem cells behave differently. Instead of listening to their…

In most animals, stem cells rely on nearby cells to tell them what to do. However, new research from the Stowers Institute for Medical Research shows that flatworm, or planarian, stem cells behave differently. Instead of listening to their…


The first-ever civil penalty award of $5.8million is one of four recent decisions signalling the OAIC’s enforcement-lead approach.
The Australian privacy landscape has undergone a significant shift, with regulators demonstrating an unprecedented willingness to pursue enforcement action and impose substantial penalties for privacy breaches. Recent decisions by the Office of the Australian Information Commissioner (OAIC) and the Federal Court, including the first ever civil penalty of $5.8M for breaching the Privacy Act, signal new era of accountability for organisations handling personal information.
The first tranche of Privacy Act reforms, passed in December 2024, has fundamentally altered the enforcement landscape. The OAIC now wields significantly broadened powers through a new three-tiered civil penalty regime that reflects the seriousness with which Parliament views privacy compliance.
Under the new framework, organisations face escalating consequences for privacy failures. Tier 1 penalties for specified administrative failures allow the Privacy Commissioner to issue infringement notices of up to $330,000 per contravention for corporations and $66,000 for individuals. Tier 2 addresses interferences with privacy that fall short of being ‘serious,’ with penalties reaching $3.3 million for corporations. Most significantly, Tier 3 penalties for serious interferences with privacy now carry maximum penalties of $50 million, three times the value of any benefit obtained, or 30% of adjusted turnover during the relevant period.
Additional reforms already in effect include requirements for notification of automated decision-making involving personal information, the introduction of technical and organisational measures to protect personal information as a compliance framework, and offences for doxxing. The new statutory tort for serious invasions of privacy is now also in force, allowing individuals to bring damages claims against a wrongdoer where that person intrudes on the ‘individual’s seclusion’ or that person ‘misuses information’ that relates to the individual, which is defined to include collecting, using or disclosing information about the individual (see here for more details).
Australian Privacy Principle 11 forms the cornerstone of data security obligations under the Privacy Act 1988. APP 11.1 requires that APP entities, which includes businesses and not-for-profits with more than $3M annual revenue, must take ‘reasonable steps’ to protect personal information they hold from misuse, interference and loss, and from unauthorised access, modification or disclosure. Additionally, APP 11.2 requires entities to destroy or de-identify personal information in certain circumstances when it is no longer needed.
The concept of ‘reasonable steps’ is deliberately flexible and dependent on context. What constitutes reasonable protection for a small business holding limited customer contact details will differ significantly from what is required of a healthcare provider managing sensitive medical records for hundreds of thousands of patients. The assessment is always made ‘in the circumstances,’ taking into account factors such as the sensitivity of the information, the volume of data held, the potential harm if the information were compromised, the size and resources of the organisation, and the current threat environment. Until the recent decision in the Office of the Australian Information Commissioner v Australian Clinical Labs, discussed further below, there has however been no judicial guidance on what ‘reasonable steps in the circumstances’ required in practice.
APP 11 does not prescribe specific technical measures or security standards. Instead, it requires organisations to assess their particular circumstances and implement appropriate safeguards.
The first tranche of privacy reforms in late 224 also introduced a significant enhancement to APP 11, with the concept of ‘reasonable steps’ now expressly including ‘technical and organisational measures’ to protect personal information. This amendment, which commenced in December 2024, elevates the importance of APP 11 compliance and aligns Australia’s privacy framework with international standards such as the European Union’s General Data Protection Regulation (GDPR).
While APP 11 still requires organisations to take ‘reasonable steps in the circumstances,’ the law now makes explicit what was previously implicit: that data security cannot be achieved through technology alone. When assessing what constitutes reasonable steps, organisations must now demonstrate they have considered and implemented both.
The ACL case, decided after these reforms commenced, demonstrates that even without the amendments, inadequate organisational measures will attract the same scrutiny and penalties as failures of technical security.
The Australian Clinical Labs (ACL) decision1 has become the touchstone for understanding APP 11 obligations in the modern cybersecurity environment. On 29 September 2025, ACL agreed to pay a $5.8 million penalty following a 2022 data breach affecting 223,000 customers. The OAIC’s successful prosecution alleged serious and systemic failures that left ACL vulnerable to cyberattack, exposing sensitive personal health information.
Under the civil penalty regime, the settlement needed to be approved by the Federal Court to ensure the penalty was legally justified, within the appropriate range and publicly accountable.
The Court’s decision was delivered by Justice Halley on 8 October 2025. The Court imposed three separate penalties that together illustrate the full spectrum of obligations when handling personal information. ACL was penalised $4.2 million for breaching APP 11 (failure to take reasonable steps in the circumstances to protect personal information), $800,000 for breaching section 26WH(2) (failure to carry out a reasonable and expeditious assessment of whether a data breach had occurred), and $800,000 for breaching section 26WK(2) (failure to make a statement about the data breach setting out specific required information). This breakdown demonstrates that significant penalties can arise not only from the security failures that enable a breach, but also from inadequate response once a breach is discovered. Organisations must have robust incident response capabilities to ensure they can promptly assess breaches and comply with notification obligations under the Notifiable Data Breaches scheme. Importantly, the parties agreed that the breach was sufficiently serious it should have been notified within 2-3 days, and the Court agreed.
Justice Halley’s judgment provides crucial guidance on what constitutes ‘reasonable steps’ under APP 11.1. The Court found that circumstances requiring consideration include the sensitivity of personal information, potential harm to individuals, the size and sophistication of the organisation, the prevailing cybersecurity environment, and any previous threats or attacks.
The specific deficiencies identified in ACL’s security posture included failing to implement application whitelisting to prevent unauthorised programs from running, behavioural-based analysis to detect malicious activities that might evade antivirus products, and the failure to deploy Data Loss Prevention tools on affected systems. Multi-factor authentication was not required for VPN access, and firewall logs were retained for only one hour, limiting security monitoring capabilities.
From a governance perspective, the Court accepted that ACL’s incident response playbooks lacked clear role definitions and contained limited detail on containment processes. It further found that testing of incident management procedures had been inadequate following the acquisition of the relevant IT systems and the IT Team Leader responsible for incident response had received no formal cybersecurity training and had never used the incident response playbooks provided. The decision underscores that technical measures alone are insufficient; organisations must also implement robust governance frameworks, training programs, and incident response capabilities.
Another noteworthy aspect of the case is that the findings against ACL involved one part of its business only, which had belonged to Medlabs, an entity purchased by ACL roughly three months prior to the cyber incident. The decision therefore also has important implications for cybersecurity due diligence during M&A activity and the importance of promptly and effectively integrating technology systems post-acquisition.
Most recently, on 23 October 2025 the Privacy Commissioner found that online wine wholesaler Vinomofo interfered with the privacy of almost one million individuals by failing to take reasonable steps to protect the personal information it held from security risks which ultimately lead to a data breach.4 In particular, the Commissioner founds that Vinomofo could have taken the following steps:
The OAIC’s investigations into Bunnings Group Limited2 and Kmart Australia Limited3 have also established clear boundaries around the deployment of surveillance technologies, even when motivated by legitimate business objectives such as fraud prevention and safety.
Between June 2020 and July 2022, Kmart collected personal and sensitive information using facial recognition technology in 28 stores to detect refund fraud. Similarly, between November 2018 and November 2021, Bunnings deployed facial recognition in 68 stores, capturing the faces of all shoppers for comparison against a database of identified risks.
In determinations issued by the Privacy Commissioner in October 2025 and September 2025, both organisations were found to have breached multiple Australian Privacy Principles. Under APP 1, they failed to include information about facial recognition technology in their privacy policies and did not implement adequate practices and procedures for compliance. Under APP 3, they collected sensitive information without consent, as no applicable exception justified the collection. Under APP 5, they failed to take reasonable steps to notify individuals about the collection of their biometric information.
Privacy Commissioner Carly Kind’s statement accompanying these determinations articulated a crucial principle: ‘Customer and staff safety, and fraud prevention and detection, are legitimate reasons businesses might have regard to when considering the deployment of new technologies. However, these reasons are not, in and of themselves, a free pass to avoid compliance with the Privacy Act.’
The message is clear – organisations must conduct thorough privacy impact assessments before deploying surveillance technologies, obtain genuine consent for the collection of sensitive information, ensure privacy policies accurately reflect data handling practices, and consider whether less intrusive alternatives could achieve the same business objectives.
The recent enforcement actions and regulatory reforms require a thoughtful and considered response from organisations handling personal information. Boards and executive leadership should prioritise cybersecurity governance, ensuring that technical and organisational measures are commensurate with the sensitivity and volume of personal information held. Regular testing of incident response procedures, meaningful security awareness training for all staff, and engagement of appropriately qualified cybersecurity personnel are no longer optional.
Before deploying any new technology that collects or uses personal information, organisations must conduct thorough privacy impact assessments and ensure privacy policies accurately reflect actual data handling practices. Where sensitive information is involved, genuine consent must be obtained unless a specific exception applies.
The clear message from recent enforcement action is that accountability in privacy and cybersecurity is no longer aspirational – it is expected, scrutinised, and rigorously enforced. Organisations that fail to prioritise privacy compliance do so at significant financial, legal and reputational risk.
For further information about privacy compliance obligations or assistance with cyber incident response plans, privacy impact assessments and governance frameworks, or please contact our Cyber and Privacy team.
1 Australian Information Commissioner v Australian Clinical Labs Limited (No 2) [2025] FCA 1224
2 Commissioner initiated investigation into Bunnings Group Limited (Privacy) [2024] AICmr 230 (29 October 2024)
3 Commissioner Initiated Investigation into Kmart Australia Limited (Privacy) [2025] AICmr 155 (26 August 2025)
4 Commissioner Initiated Investigation into Vinomofo Pty Ltd (Privacy) [2025] AICmr 175 (17 October 2025)

Our second article for Cyber Security Awareness Month explores the increasing convergence of cyber risk and financial lines exposures, evidenced by recent ASIC actions.
Cybersecurity failures are no longer viewed solely as technical issues, they are being treated as governance and compliance failures, with significant implications for directors, officers, and financial lines insurers. In this article we consider recent ASIC civil penalty proceedings, offering guidance on what constitutes ‘reasonable’ cyber risk management in the eyes of the regulator.
Australian Financial Services (AFS) licensees have a general obligation to provide efficient, honest and fair financial services. They must comply with the conditions of their AFS licence and obligations under the Corporations Act 2001 (Cth)(Corporations Act).
As an AFS licensee, your obligations under s 912A(1) include the following:
| Section 912A(1)(a) | do all things necessary to ensure that the financial services covered by the licence are provided efficiently, honestly and fairly |
| Section 912A(1)(d) | have available adequate resources (including financial, technological and human resources) to provide the financial services covered by the licence and to carry out supervisory arrangements |
| Section 912A(1)(f) | ensure that its representatives are adequately trained and are competent, to provide those financial services |
| Section 912A(1)(h) | have adequate risk management systems |
If you are an AFS licensee, you must be mindful of the nature of your business, the nature and extent of the information you hold, and the value of the assets you hold when assessing the risk of adverse consequences for you and your clients. In today’s landscape, AFS licensees are subject to the risk of a cyber incident, loss of ability to provide financial services, unauthorised impersonation of you or your clients to third parties, direct or indirect financial loss, theft of confidential or personal information, and potential exposure to civil penalties and claims for damages.
You can best protect yourself by ensuring your financial services are provided efficiently, honestly and fairly (s 912A(1)(a)) through adequate cybersecurity measures and adequate resources (s912A(1)(d)), and adequate risk management systems (s 912A(1)(h)). If you have authrorised representatives (Ars), ensure they are adequately trained and competent to provide the financial services covered by the licence (s 912A(1)(f)).
To meet your obligations under s 912A(1)(a), adequate cybersecurity measures are those that are in place to protect its clients from the risks and consequences of a cyber intrusion. These measures should be proportionate to the nature, scale, and complexity of the business and the sensitivity of the information it holds. This includes implementing appropriate technical controls, maintaining up-to-date systems and software, and having clear policies and procedures for detecting, responding to, and recovering from cyber incidents.
To meet your obligations under s 912A(1)(d), a business must ensure it has adequate financial, technological and human resources. The key focus here is on ensuring that appropriate technical cybersecurity measures are in place, supported by the presence of an employee with the necessary technical expertise to implement, monitor, and maintain those measures and the broader risk management systems.
Under s 912A(1)(h), this means a risk management system that adequately identifies and evaluates the risks posed which result in the AFSL holder being able to adopt controls to manage or mitigate those risks to a reasonable level. While the standard of “adequacy” is ultimately one for the Court to decide, the Court’s assessment of the adequacy of any particular set of cyber risk management systems will likely be informed by evidence from relevantly qualified experts in the field.
In 2022 ASIC, the corporate regulator, was successful in civil penalty proceedings against RI Advice, however until recently there had been few material developments in this area. Recent ASIC civil penalty proceedings over the last few months, however, show that the regulator is continuing its enforcement approach.
In Australian Securities and Investments Commission v RI Advice Group Pty Ltd [2022] FCA 496, the Federal Court found Australian Financial Services licensee, RI Advice, breached its license obligations under s 912A(1)(a) to act efficiently and fairly when it failed to have adequate risk management systems under s 912A(1)(h) to manage its cybersecurity risks.
The finding comes after a significant number of cyber incidents occurred at authorised representatives (ARs) of RI Advice between June 2014 and May 2020. Of importance, RI Advice needed to identify the risks that the ARs faced in the course of providing financial services pursuant to RI Advice’s licence, including in relation to cybersecurity and cyber resilience, and have documentation, controls and risk management systems in place that were adequate to manage risk in respect of cybersecurity and cyber resilience across the AR network. Although most of the historic issues (poor password practices, and lack of up-to-date antivirus software, or filtering or quarantining of emails) were later addressed by significant improvements in 2021, the Court found that RI Advice’s steps to remediate were inadequate and should have been addressed much earlier.
In line with Her Honour Justice Rofe’s decision, AFS licensees need to be mindful that it is possible to materially reduce cybersecurity risk through adequate cybersecurity documentation and controls to an acceptable level.
In ASIC v FIIG Securities Limited2, ASIC alleges that FIIG’s conduct exposed FIIG and its clients to the risk of cyber intrusion and the adverse consequences to a heightened and unreasonable extent. ASIC alleges that if FIIG had adequate cybersecurity measures, it would have detected suspicious activity on its network and identified the compromise, and therefore could have prevented the threat actor’s access, download and publication of the stolen data. In total, ASIC alleges FIIG contravened one or more of the ss 912A(1)(a), 912A(1)(d), 912A(1)(h), 912A(5A).
In the most recent civil penalty proceedings commenced by ASIC against Fortnum Private Wealth Ltd,3 ASIC alleges that the volume and sensitivity of personal information collected by Fortnum in the course of its business highlighted the critical need to identify and mitigate cybersecurity risks, both within the organisation and among its ARs. ASIC’s allegations highlightthe importance of having robust policies, frameworks, systems, and controls in place to effectively manage those risks.
Despite being an attractive target for threat actors and facing a heightened risk of cyber-related attacks, ASIC alleges Fortnum failed to:
Overall, ASIC alleges that Fortnum breached sections 912A(1)(a) and 912A(5A) of the Corporations Act by failing to implement an adequate cybersecurity policy to manage and mitigate cyber risks affecting both the business and its ARs. ASIC also alleges Fortnum failed to provide adequate cybersecurity education or training, and did not establish effective processes, systems, or frameworks to oversee and monitor its ARs in relation to cybersecurity risk and resilience.
Both FIIG Securities Limited and Fortnum Private Wealth Ltd deny the allegations.
To avoid breaching AFSL obligations, businesses must adopt a proactive, well-resourced, and risk-aware compliance approach. This includes implementing strong governance, risk management, and compliance frameworks that reflect the scale and complexity of business operations. With cyber threats posing a growing risk to financial services, businesses must also embed cybersecurity into their compliance strategy, ensuring systems, data, and client information are protected through robust controls and incident response planning. Competent personnel, regular monitoring, and a culture of accountability are essential to maintaining compliance and meeting ASIC’s expectations under the Corporations Act.
Have a documented proportionate and implemented cybersecurity risk management framework (policies, procedures, standards) and adequate resourcing, to ensure it is properly complied with.
Implement baseline technical controls such as firewalls, patching, MFA, backups, and logging, and enforce people and process controls, including mandatory security awareness and role-specific training.
Engage skilled cyber experts to assess the risks faced by your business in its operations and IT environment and ensure you have incident response plan readily available.
1“The head of the Australian Signals Directorate is calm in a crisis and thrives amid chaos”, Qantas magazine, October 2025, p189.
2ASIC’s Concise Statement
3The Originating Process and Concise Statement

OpenAI has launched ChatGPT Atlas, a new web browser built with ChatGPT at its core, enabling it to serve as an AI-powered assistant that integrates into users’ usual browsing flow, understands context, and responds in natural…

It’s a well-known fact that Jupiter plays a vital role in the dynamics of the Solar System. As the largest planet beyond the “Frost Line,” the boundary where volatiles (like water) freeze, Jupiter protects the planets of the inner Solar…

Adults who suffer from gum disease could be more likely to show signs of injury in the brain’s white matter, according to new research published on October 22, 2025, in Neurology® Open Access, a journal of the American Academy of Neurology….