Sucker Punch’s latest entry in the Ghost franchise, Ghost of Yotei, has reportedly sold over 1.6 million copies so far.
According to Alinea…

Sucker Punch’s latest entry in the Ghost franchise, Ghost of Yotei, has reportedly sold over 1.6 million copies so far.
According to Alinea…

The first step to solving a problem is understanding it, and a common worldwide phenomenon wasn’t properly understood until shockingly recently. With the aid of satellites, researchers can now accurately track the state of the world’s glaciers.

▲ The Frame displaying “Metamorphosis of Narcissus” by Salvador Dalí
Samsung…
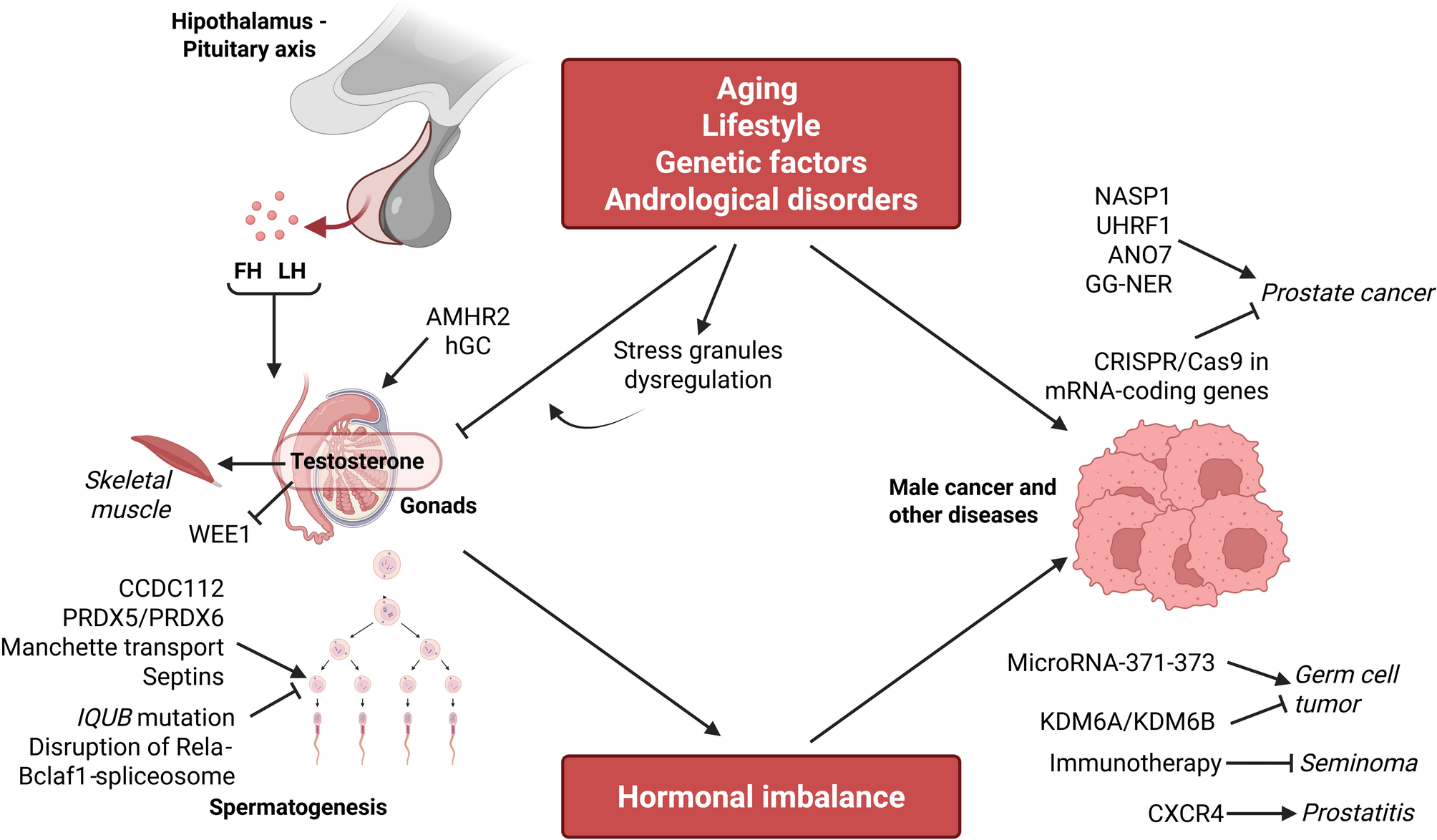
Endocrinology of the Testis. and Male Reproduction | SpringerLink [Internet]. [cited 2025 Jul 23]. Available from: https://link.springer.com/https://doi.org/10.1007/978-3-319-44441-3
Jahangir M, Nazari M, Babakhanzadeh E, Manshadi SD. Where do obesity and male infertility collide? BMC Med Genom. 2024;17:128.
Google Scholar
Zhang Y, Song J-Y, Sun Z-G. Exploring the impact of environmental factors on male reproductive health through epigenetics. Reprod Toxicol. 2025;132:108832.
Google Scholar
Bracke A, Peeters K, Punjabi U, Hoogewijs D, Dewilde S. A search for molecular mechanisms underlying male idiopathic infertility. Reprod Biomed Online. 2018;36:327–39.
Google Scholar
Heck AL, Handa RJ. Sex differences in the hypothalamic–pituitary–adrenal axis’ response to stress: an important role for gonadal hormones. Neuropsychopharmacol. 2019;44:45–58.
Google Scholar
Sheng JA, Bales NJ, Myers SA, Bautista AI, Roueinfar M, Hale TM, et al. The Hypothalamic-Pituitary-Adrenal axis: Development, programming actions of Hormones, and Maternal-Fetal interactions. Front Behav Neurosci. 2020;14:601939.
Google Scholar
Rebello RJ, Oing C, Knudsen KE, Loeb S, Johnson DC, Reiter RE, et al. Prostate cancer. Nat Rev Dis Primers. 2021;7:9.
Google Scholar
Ng KL. The Etiology of Prostate Cancer. In: Bott SR, Ng KL, editors. Prostate Cancer [Internet]. Brisbane (AU): Exon Publications; 2021 [cited 2025 Jul 14]. Available from: http://www.ncbi.nlm.nih.gov/books/NBK571322/
Fichtner A, Nettersheim D, Bremmer F. Pathogenesis and pathobiology of testicular germ cell tumours: a view from a developmental biological perspective with guidelines for pathological diagnostics. Histopathology. 2024;85:701–15.
Google Scholar
Fichtner A, Richter A, Filmar S, Gaisa NT, Schweyer S, Reis H, et al. The detection of isochromosome i(12p) in malignant germ cell tumours and tumours with somatic malignant transformation by the use of quantitative real-time polymerase chain reaction. Histopathology. 2021;78:593–606.
Google Scholar
Stuppia L, Franzago M, Ballerini P, Gatta V, Antonucci I. Epigenetics and male reproduction: the consequences of paternal lifestyle on fertility, embryo development, and children lifetime health. Clin Epigenetics. 2015;7:120.
Google Scholar
Van Cauwenbergh O, Di Serafino A, Tytgat J, Soubry A. Transgenerational epigenetic effects from male exposure to endocrine-disrupting compounds: a systematic review on research in mammals. Clin Epigenetics. 2020;12:65.
Google Scholar
Gentile G, De Stefano F, Sorrentino C, D’Angiolo R, Lauretta C, Giovannelli P, et al. Androgens as the old age stick in skeletal muscle. Cell Communication Signal. 2025;23:167.
Google Scholar
Li J, Shen L, Wang K, Wu S, Wang Y, Pan Y, et al. Biogenesis of stress granules and their role in the regulation of stress-induced male reproduction disorders. Cell Communication Signal. 2025;23:84.
Google Scholar
Löf C, Sultana N, Goel N, Heron S, Wahlström G, House A, et al. ANO7 expression in the prostate modulates mitochondrial function and lipid metabolism. Cell Communication Signal. 2025;23:71.
Google Scholar
Zhang Y, Zhang C, Feng R, Meng T, Peng W, Song J, et al. CXCR4 regulates macrophage M1 polarization by altering Glycolysis to promote prostate fibrosis. Cell Communication Signal. 2024;22:456.
Google Scholar
Li Z, Wang Y, Yu Z, Luo Y, Zhao Y, Xue E, et al. UHRF1 phase separation mediates stable inheritance of DNA methylation and promotes the proliferation of prostate cancer cells. Cell Communication Signal. 2025;23:297.
Google Scholar
Feng Y, Sun J, Kang X, Wang Y, Liu K, Wang W, et al. NASP implication in the androgen receptor associated with castration resistance in prostate cancer. Cell Communication Signal. 2025;23:331.
Google Scholar
Zhong C, Wang J, Peng H, Lu J, Long Z, Lin Z, et al. GG-NER’s role in androgen receptor signaling inhibitor response for advanced prostate cancer. Cell Communication Signal. 2024;22:600.
Google Scholar
Shokry D, Khan MW, Powell C, Johnson S, Rennels BC, Boyd RI, et al. Refractory testicular germ cell tumors are highly sensitive to the targeting of polycomb pathway demethylases KDM6A and KDM6B. Cell Commun Signal. 2024;22:528.
Google Scholar
Tavares NT, Lourenço C, Constâncio V, Fernandes-Pontes F, Fonseca D, Silva-Santos R, et al. MicroRNA-371–373 cluster extracellular vesicle-based communication in testicular germ cell tumors. Cell Communication Signal. 2025;23:252.
Google Scholar
Cui Y, Zhou X, Zhang J, Fang B, Ge J, Tang H, et al. Exploiting potential molecular compounds for treating testicular seminoma by targeting immune related genes. Cell Communication Signal. 2024;22:560.
Google Scholar
Tabibian M, Moghaddam FS, Motevaseli E, Ghafouri-Fard S. Targeting mRNA-coding genes in prostate cancer using CRISPR/Cas9 technology with a special focus on androgen receptor signaling. Cell Communication Signal. 2024;22:504.
Google Scholar
Zhao H, Li J, Xiao Z, Xiao Y. Dose-dependent role of AMH and AMHR2 signaling in male differentiation and regulation of sex determination in Spotted knifejaw (Oplegnathus punctatus) with X1X1X2X2/X1X2Y chromosome system. Cell Communication Signal. 2025;23:59.
Google Scholar
Zhai W, Tian H, Liang X, Wu Y, Wen J, Liu Z, et al. Androgen blockage impairs proliferation and function of Sertoli cells via Wee1 and Lfng. Cell Communication Signal. 2024;22:498.
Google Scholar
Gao T, Liu Y, Li J, Zhang Y, Wu B. Function of Manchette and intra-manchette transport in spermatogenesis and male fertility. Cell Communication Signal. 2025;23:250.
Google Scholar
Zhou H, Xu Z, Jiang C, Wu Q, Zhang C, Liu Z, et al. Ionizing radiation-induced disruption of Rela-Bclaf1-spliceosome regulatory axis in primary spermatocytes causing spermatogenesis dysfunction. Cell Communication Signal. 2025;23:58.
Google Scholar
Agnieszka M-M, Magdalena B-N, Mariola S, Andrzej C. PRDX5 and PRDX6 translocation and oligomerization in bull sperm: a response to cryopreservation-induced oxidative stress. Cell Communication Signal. 2025;23:15.
Google Scholar
Graffeo ML, Nguyen J, Parast FY, Dunleavy JEM, Korneev D, Yang H, et al. A novel mechanism of sperm midpiece epididymal maturation and the role of CCDC112 in sperm midpiece formation and Establishing an optimal flagella waveform. Cell Communication Signal. 2025;23:319.
Google Scholar
Hu T, Tang X, Ruan T, Long S, Liu G, Ma J, et al. IQUB mutation induces radial spoke 1 deficiency causing asthenozoospermia with normal sperm morphology in humans and mice. Cell Communication Signal. 2025;23:41.
Google Scholar
Al-Ali H, Baig A, Alkhanjari RR, Murtaza ZF, Alhajeri MM, Elbahrawi R, et al. Septins as key players in spermatogenesis, fertilisation and pre-implantation embryogenic cytoplasmic dynamics. Cell Communication Signal. 2024;22:523.
Google Scholar
Errico A, Ambrosini G, Vinco S, Bottani E, Dalla Pozza E, Marroncelli N, et al. In vitro effect of hCG on Cryptorchid patients’ gubernacular cells: a predictive model for adjuvant personalized therapy. Cell Communication Signal. 2025;23:19.
Google Scholar

An article by Dmitry Marinov, CTO of ANY.RUN, a UAE-based cybersecurity company
As the MENA startup ecosystem matures, cybersecurity has shifted from a back-office concern to a boardroom topic. With investors now demanding tangible proof of security controls—and not just compliance claims—founders must treat cybersecurity as a marker of operational maturity, not an afterthought.
In 2025, MENA startups face mounting pressure to align with both domestic compliance regimes (such as the UAE’s TDRA/NCA and KSA’s SAMA/NCA frameworks) and global investor expectations tied to ISO 27001, SOC2, and GDPR-like standards.
What’s new is that these aren’t just policies on paper — they now demand proof of practice. Startups are expected to demonstrate:
If just three years ago regional VCs rarely asked about security during due diligence, today investors and auditors increasingly treat this data as evidence of operational maturity, not just hygiene.
Still, the gap between what investors expect and what is happening on the ground has never been wider. In my incident response work across the MENA region, I’ve seen the same pattern repeatedly: startups with world-class products running on completely flat networks — all servers, workstations, and development environments on the same subnet with limited internal firewalls, no log retention beyond a week, and employees opening suspicious files directly on their laptops.
Becoming “security-capable” doesn’t require a fortune or a full SOC team. But it does require understanding what’s actually hitting startups in this region.
The most common types of attacks against startups in MENA
Startups everywhere face a standard set of cyber risks — phishing, ransomware, business email compromise (BEC) scams, and supply chain attacks. While Western attackers often aim to exfiltrate data at scale, many MENA-targeted campaigns are financially driven, delivering loaders like PrivateLoader or SmokeLoader as access points for ransomware groups.
Startups in the UAE and Saudi Arabia face disproportionately high volumes of commodity malware, rarely seen in ecosystems like those in the EU and the US. The region exhibits a distinctive flavour and intensity in specific vectors:
Common root causes and security blind spots in early-stage teams
The biggest misconception among startups is that security is a “scale problem”—something to worry about after product-market fit. In reality, security debt compounds like technical debt, and the longer you wait, the more it costs—in engineering time, customer trust, and valuation risk.
Attackers don’t wait for Series B funding. We’ve seen phishing kits and loaders hit within days of a product launch, especially in regions like MENA where sandboxing and logging practices are still maturing.
Investors are also asking earlier: by the time you’re raising your first institutional round, funds in Abu Dhabi or Riyadh are already requesting red-team reports and sandbox logs. The tipping point isn’t a breach — it’s your first customer. From the moment you handle user data or payment flows, you’re a target, whether you have 50 users or 50,000.
Across early-stage startups, the same weaknesses surface repeatedly:
A consistently overlooked mistake is lacking a safe place to open suspicious files. This doesn’t require a full-blown SOC or complex infrastructure — just a browser-based sandbox that lets your team safely detonate files in isolation.
Tools that enable this are easy to implement, yet many teams skip them entirely, assuming antivirus or email filters are “good enough.”
As a result, a single PDF or ZIP can slip through and trigger a compromise, especially where access controls are weak. Ultimately, it’s not just about detection — it’s about instilling a habit and providing a platform for your team to verify files before trusting them.
Practical security moves for small teams
Even without a dedicated SecOps function, early-stage startups can now reach higher levels of security maturity thanks to accessible, lightweight tools:
These practices don’t just close security gaps—they can also make a startup more credible to investors and partners. Keeping sandbox logs and IOC reports from suspected incidents shows that detection and response aren’t just aspirational.
A simple security whitepaper outlining key controls — identity management, backups, incident response — gives partners and investors clarity about how you operate. Regularly auditing third-party dependencies, especially open-source libraries, and pinning versions reduces supply-chain risk. And when your response plans are not only documented but also practised and version-controlled, it signals the kind of operational maturity investors value.
Five-step starter playbook for cybersecurity at a startup
Startups don’t need to build enterprise-grade security overnight, but a few foundational practices can make a dramatic difference in both security maturity and credibility.
These steps will not only reduce the likelihood of a breach but also build trust with users, speed up procurement, and make due diligence smoother when you’re raising capital.

Donald Trump and Egyptian president Abdel Fattah al-Sisi will co-host a summit of more than 20 world leaders in Sharm El Sheikh on Monday, after the US president first visits Israel to speak at the Knesset and meet families of the hostages.
The…

It seems good things really do come to those who wait! For the final day of its October Prime Day sale in Australia, Amazon’s unlocked an extra discount on the Award-winning Sony WF-C510 earbuds that brings them to their lowest ever price in…

Scientists have discovered a unique signature of chronic fatigue syndrome, also known as myalgic encephalomyelitis (CFS/ME), in the blood of patients with severe symptoms.
Using no fewer than 200 blood biomarkers, researchers at the…

What started as a social media experiment, writer/director/star Jon Fletcher has wrapped his feature debut The Dosage Makes the Poison.
Fletcher (who has acted on Bosch, The Rook, The Messengers) completed the seven-day shoot,…

As a general rule each week, public bettors tend to back favorites — both on the spread…