In July, William Cartwright was playing club rugby. Four months later, the Australian had played his part in his side reaching the men’s final on the first stop of the 2025/26 HSBC SVNS Series in a showdown against arch-rivals New Zealand.
An…

In July, William Cartwright was playing club rugby. Four months later, the Australian had played his part in his side reaching the men’s final on the first stop of the 2025/26 HSBC SVNS Series in a showdown against arch-rivals New Zealand.
An…

Spinal infectious diseases are caused by pathogenic microorganisms invading the spine and surrounding tissues, with incidence of 0.5 to 2.5 cases per 100,000 people.1–3 Population aging, high prevalence of chronic diseases as…
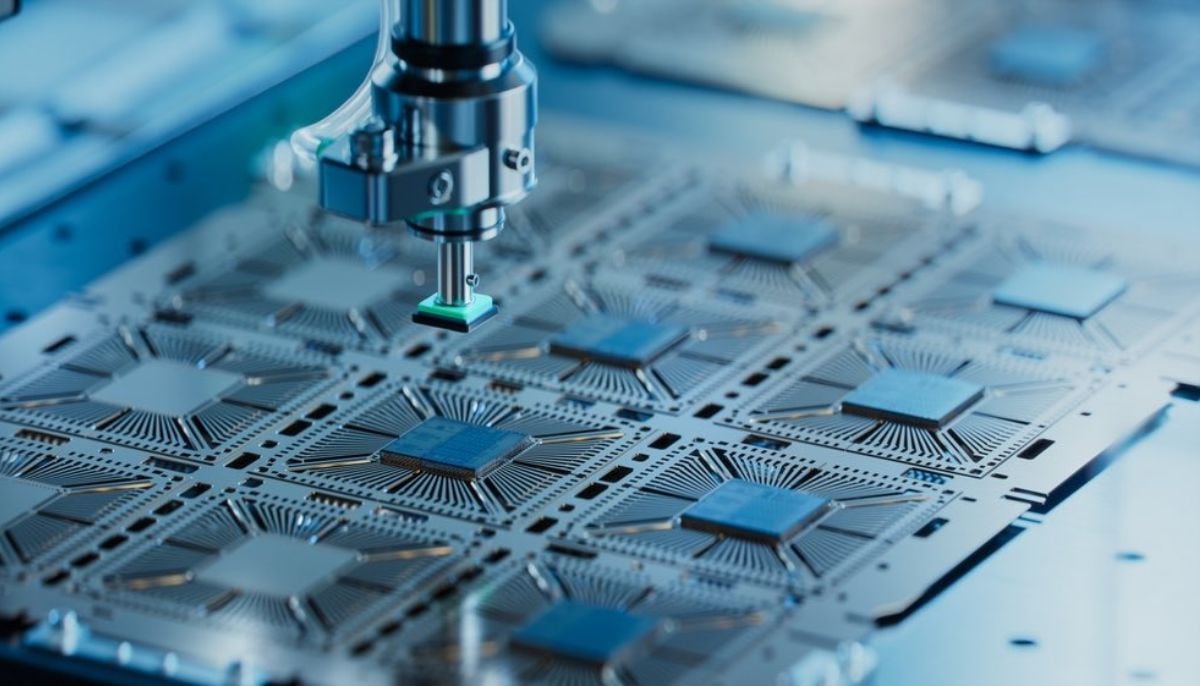
Scientists in a recent breakthrough have achieved the “highest hole…

The paper discusses Bulgaria’s public investment needs and its efficiency and assesses prospects for accelerating economic growth and income convergence through scaling up quality public investment. Utilizing substantial EU grants to fund public investment offers Bulgaria a unique opportunity to finance important infrastructure projects without relying on debt. However, slow absorption of these grant funds and inefficiencies in public investment management remain significant challenges. The analysis highlights the critical role of efficient public investment in boosting productivity and fostering sustainable growth. Using the DIGNAR model calibrated to Bulgaria’s economy, simulations suggest that full EU funds absorption and improved public investment efficiency could boost GDP by 2.3 percent in 2030. The findings underscore the importance of steadfast reforms to accelerate EU fund absorption and improve efficiency, including through enhanced investment planning and procurement processes, to boost growth.
Subject: Econometric analysis, Expenditure, General equilibrium models, Income, Infrastructure, National accounts, Public investment spending
Keywords: Bulgaria, DIGNAR model, dynamic general equilibrium modelling, economic growth, EU funds, General equilibrium models, Income, Infrastructure, public investment, Public investment spending

The final full moon of 2025 treated stargazers to a high-flying lunar spectacle as the “Cold Moon” glowed among the stars of the constellation Taurus on Dec. 4.
December’s full moon was the third in a string of “Supermoons” — full moons that…

Instructs relevant govt bodies to work with protestors, explain benefits of projects under scrutiny
The Lahore High Court has raised strong objections…

If you’re a woman, you likely have your own stories about menstrual discomfort. Dealing with cramps, irritability, and bloating can be challenging each month. Many women use over-the-counter pain relievers to help. However, some natural…

When HMS Pinafore premiered in 1878, audiences would have appreciated a particularly topical lampoon skewering the First Lord of the Admiralty, WH Smith, a man who, much like Gilbert’s Sir Joseph Porter, ascended the greasy pole of politics…

With 2025 coming to a close, our editors had the difficult task of summing up the year in culture. For this Friday’s episode of The Run-Through, we invited Vogue’s deputy editor, Taylor Antrim, and senior editor Marley Marius to run through…