- Eight militants killed in joint operation in Pakistan’s northwest, military says Arab News
- Security forces kill 8 terrorists in Bannu IBO: ISPR Dawn
- Securing the Frontline The Nation (Pakistan )
- Five terrorists killed in Bannu IBO The Express…
Author: admin
-
Eight militants killed in joint operation in Pakistan’s northwest, military says – Arab News
-

Pakistan lifts ban on gold import and export after cabinet’s go-ahead
Gold bars are stacked in the safe deposit boxes room of the Pro Aurum gold house in Munich, Germany, January 10, 2025. — Reuters - May 2025 suspension of 2013 precious metals order rescinded.
- Entrustment Scheme’s…
Continue Reading
-

Parent diets around conception leave lasting marks on baby’s DNA
Our earliest environment is a swirl of nutrients around a dividing embryo in the days just after conception. A new scientific article argues that what parents eat during that period can rewrite chemical tags on their baby’s DNA, nudging…
Continue Reading
-

Greenwich tenants had to urinate in bath when left with no loo
Residents of a shared property in south-east London had to urinate in a bath or use the lavatories at a nearby furniture superstore for 58 days because their landlord did not fix a broken toilet, a tribunal has heard.
The five tenants also had to put up with a faulty ventilation system that was so noisy it kept them awake at night and caused mould.
They applied for rent repayment accusing the landlords of not holding the correct licence to run the Greenwich property and were given £5,300 back.
The landlord accepted they were unlicensed and said it was due to the co-landlord’s memory loss which they had experienced since suffering a “severe brain injury” in 2021.
The owners of the four-bedroom maisonette on Woolwich Road required a special licence as the property was a House in Multiple Occupation (HMO), meaning the home was shared by at least three people sharing the same kitchen and bathroom.
The landlord told the tribunal that she had lost a letter from Greenwich Council which outlined updates to the council’s licensing policy, the Local Democracy Reporting Service reported.
The tribunal’s impression was that both landlords’ understanding of the licensing regime was limited and “they had no real understanding of the nature of mandatory licensing”.
The tribunal acknowledged the landlord’s health situation, but ruled they should have been aware of the need for HMO licensing as they owned and managed other HMO properties.
One of the residents admitted to breaking the lavatory bowl in October 2023. The landlords accepted responsibility for the repair, but it was not carried out for 58 days, the tribunal heard.
The landlords said they thought the faulty ventilation system served the whole block, but after finding out this was not the case a specialist company was contacted to have the system checked and repaired.
The system was found to be operating at 50 per cent efficiency and vent openings within the flat were “seriously affected by mould”, according to a report from the proceedings.
Considering the licensing, disrepair and other issues, the tribunal calculated the Rent Repayment Order to be 40 per cent of the maximum possible figure of £13,229. This was rounded to £5,300.
Continue Reading
-

The New Perrelet x Diaa Allam Launches at Dubai Watch Week
Now a key event on the global watch calendar, Dubai Watch Week celebrates its seventh edition this year with over 90 brands. Like some of the participating brands, Perrelet has created a special edition for the event that…
Continue Reading
-

Grafana Unveils Smarter Logs, an MCP Server, and TraceQL Upgrades in Latest Releases
Grafana Labs has published major updates across two of its core observability products: Grafana 12.3, and Grafana Tempo 2.9. The two releases have distinct improvements in monitoring and tracing for Grafana users.
Grafana 12.3 adds…
Continue Reading
-

NPR’s Book of the Day : NPR
Amy and Nick Dunn have the perfect life and are the perfect couple until they reach a breaking point, revealing their true selves. The book that spawned dozens…
Continue Reading
-
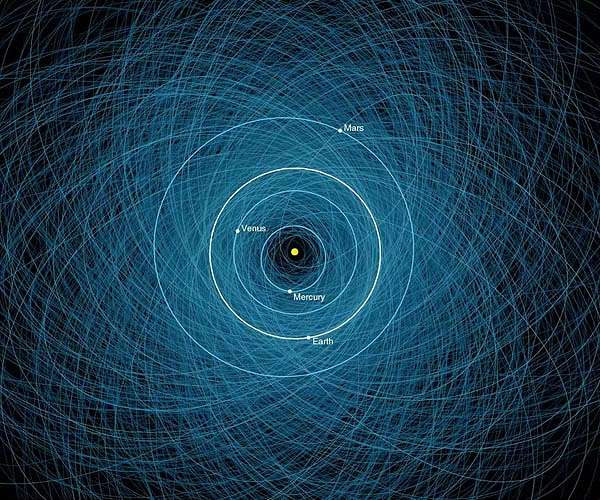
40 000 near-Earth asteroids discovered!
by ESA Staff Writers
Paris, France (ESA) Nov 21, 2025
Astronomers recently discovered the 40 000th near-Earth asteroid! These space rocks range from a few metres to a few kilometres in size and are on orbits that bring them…
Continue Reading
-

Worms to be sent to ISS for space medicine experiment in 2026
by Sophie Jenkins
London, UK (SPX) Nov 21, 2025
Scientists at Space Park Leicester have developed a compact laboratory known as the Petri Pod for biological experiments in space. This hardware, created in collaboration with the…
Continue Reading
-

Plasmasphere compressed by recent geomagnetic superstorm dramatically slowed recovery
by Riko Seibo
Tokyo, Japan (SPX) Nov 21, 2025
Researchers have detailed how a geomagnetic superstorm on May 10-11, 2024, shrank Earth’s plasmasphere, a protective zone of charged particles, to just one-fifth of its normal size. The…
Continue Reading